Understanding CISSP Domain 3: Security Architecture and Engineering - Part 3
In part 1 of Domain 3, Security Architecture and Engineering, we covered topics such as secure design principles, models, selecting controls, and mitigating system vulnerabilities. In part 2, we explored cryptography and secure cryptographic solutions.
In Part 3, we delve into objectives 3.7-3.10, understanding cryptanalytic attack methods, applying secure site and facility design principles, site design and controls, and managing the information life cycle. We’ll cover the material by following the ISC2 exam outline.
3.7 - Understand methods of cryptanalytic attacks
Cryptanalytic attacks are methods used to circumvent the security of a cryptographic system and gain access to encrypted information (plaintext) without possessing the secret key. This process, also known as cryptanalysis or code-breaking, involves finding and exploiting weaknesses in cryptographic algorithms, protocols, or their implementations.
Brute force
A brute-force cryptanalytic attack is a method of cracking a password, passphrase, or data encryption by systematically trying every possible key combination or password until the correct one is found. It is an exhaustive search approach that relies purely on computational power.
Example: A common example involves a standard 4-digit PIN (Personal Identification Number). The possible combinations range from 0000 to 9999, for a total of 10,000 possibilities. A computer can test all of these combinations almost instantly.
Key safeguards and countermeasures include:
Strong password policies: Enforce the use of long, complex, and unique keys and passwords.
Password hashing and salting: Store passwords securely using strong, modern hashing algorithms and a unique “salt” (random data) for each password before hashing. This makes offline brute-force attacks (where attackers steal a database of hashed passwords) much more difficult.
Key stretching: Using algorithms like bcrypt, scrypt, or Argon2 to deliberately slow down the hashing process (key stretching) makes the offline testing of passwords by a brute-force attacker computationally expensive and time-consuming.
Rainbow Tables are large, precomputed databases that store chains of plaintext passwords and their corresponding cryptographic hash values. The purpose of a rainbow table is to allow an attacker who has stolen a database of hashed passwords to quickly look up a hash and retrieve the original plaintext password without having to compute hashes in real-time during the attack.
Rainbow tables are a form of time-memory trade-off used to speed up password-cracking, including brute-force and dictionary attacks.
A Dictionary Attack is a password-cracking method in which the attacker systematically tries every word in a dictionary or word list. This approach exploits the human tendency to choose predictable, easy-to-remember passwords rather than random, complex strings of characters.
Defending against dictionary attacks primarily involves enforcing strong password hygiene and implementing technical controls to detect and prevent automated guessing attempts:
Enforce policies that require long, random, and unique passwords or passphrases.
Requiring MultiFactor Authentication (MFA) is one of the most effective countermeasures.
Limit the number of failed login attempts within a specific time frame. After a set number of failures, the account should be temporarily locked or the IP address blocked.
A Hybrid Attack is a password-cracking method that combines elements of both dictionary and brute-force attacks. Its goal is to achieve a higher success rate than a pure dictionary attack while being faster than a full, exhaustive brute-force attack.
In a hybrid attack, the attacker starts with a list of common words or dictionary entries (like a dictionary attack) and then applies systematic, algorithmic variations (like a brute-force attack) to those words to generate a much larger list of potential passwords to test.
Ciphertext only
An attack where the attacker has access only to a collection of ciphertexts (encrypted messages) and attempts to determine the plaintext or the encryption key used.
This is the most basic and challenging for the attacker, as they are working with the minimum amount of information possible.
An example of a ciphertext-only attack is the interception and analysis of an encrypted message.
The primary defense against a ciphertext-only attack is to use a strong, well-vetted encryption algorithm and proper key management.
Known plaintext
Known plaintext is an attack where the attacker has access to both the plaintext of a message and its corresponding ciphertext.
The attacker analyzes the relationship between the known plaintext and the ciphertext to reverse-engineer the encryption process or, more typically, to narrow the range of possible secret keys.
A Meet-in-the-middle attack is typically a known-plaintext attack that works by performing two simultaneous, smaller brute-force searches with different keys: one forward from the plaintext and one backward from the ciphertext, until the results “meet in the middle” at a common intermediate value. When a match is found, the attack can compute the full key.
A chosen plaintext attack is a powerful attack model in cryptanalysis in which the attacker can choose specific plaintexts to be encrypted and obtain the corresponding ciphertexts.
The chosen plaintext model is a strong hypothetical scenario, and it is often relevant in real-world situations where an attacker might influence data that gets encrypted, such as:
Public-key encryption, where an attacker can use this ability to launch a chosen plaintext attack by generating ciphertexts corresponding to specific plaintexts they want to test.
Protocol design flaws, where an attacker might exploit flaws in communication protocols that encrypt user-controlled input, allowing them to effectively perform a chosen plaintext attack.
Differential Cryptanalysis, which is a powerful, general-purpose cryptanalytic attack. The main idea is to observe and exploit non-random behavior in a cipher’s internal workings. Many modern encryption standards have been designed with resistance to differential cryptanalysis in mind. Typically, a chosen plaintext attack is used to study how differences in pairs of plaintexts affect the ciphertext.
Frequency analysis
Frequency analysis is a fundamental cryptanalytic technique used to break classical ciphers by exploiting the fact that, in any given stretch of natural language, certain letters or letter combinations occur with consistently different frequencies.
Frequency analysis was a very effective manual method for breaking simple substitution ciphers for centuries. Its discovery is often attributed to the 9th-century Arab polymath Al-Kindi. However, modern cryptographic systems are designed specifically to defeat this attack by ensuring that the ciphertext appears statistically random, thereby effectively masking the plaintext's frequency patterns.
Chosen ciphertext
Chosen ciphertext is a cryptanalytic attack model in which the attacker can select a set of ciphertexts and obtain their corresponding plaintexts. An “oracle” (usually a decryption device or API) provides the decryption, allowing the attacker to learn information about the key.
The distinction between a chosen ciphertext and a chosen plaintext attack lies in which side of the encryption process the attacker can control and observe:
The standard defense in modern symmetric cryptography is to use authenticated encryption modes, which combine confidentiality (encryption) and integrity/authenticity (a Message Authentication Code, or MAC) in a single, integrated mode. The recipient first verifies the MAC of the message. If the MAC is invalid, the message is rejected immediately, and no decryption is performed, thus preventing the attacker from gaining any useful information from the decryption oracle.
A recommended approach is to use modes like AES-GCM (a mode of operation for the Advanced Encryption Standard (AES) Galois/Counter Mode), AES-EAX (an AES mode of operation that provides authenticated encryption with associated data), or AES-CCM (Counter with Cipher Block Chaining Message Authentication Code).
Here is another way to look at the four plain vs. ciphertext cryptanalytic attacks — categorized by the amount of information available to the attacker.
Ciphertext Only Attack: The cryptanalyst only has access to a collection of ciphertexts (encrypted messages). This is the most difficult scenario for an attacker.
Known Plaintext Attack: The attacker has access to a set of ciphertexts and their corresponding plaintexts. This allows the attacker to analyze their relationship and potentially deduce the encryption key or algorithm.
Chosen Plaintext Attack: The attacker can choose specific plaintexts and obtain their corresponding ciphertexts. This is a powerful model as it allows the attacker to deliberately test how the encryption system reacts to specific inputs.
Chosen Ciphertext Attack: The attacker can choose ciphertexts and obtain their corresponding plaintexts. This is used to understand the decryption process or recover the key.
Implementation attacks
An implementation attack is a type of cryptanalytic attack that targets vulnerabilities in the practical implementation (hardware, software, or operational procedures) of a cryptographic system, rather than theoretical or mathematical weaknesses in the underlying cryptographic algorithm itself.
Implementation attacks often fall under the umbrella of side-channel attacks, which exploit information that unintentionally “leaks” during the encryption or decryption process.
An example of an implementation failure is the original Wireless Encryption Protocol (WEP). The underlying RC4 encryption algorithm itself had strong mathematical properties, but the implementation in WEP was flawed because it used short, predictable Initialization Vectors (IVs). This made the system vulnerable to specific attacks that could rapidly recover the WEP key, even though the RC4 algorithm was not fundamentally broken at the time.
Side-channel
A side-channel attack aims to extract secret information (such as encryption keys, plaintext, or internal algorithm state) by analyzing unintended information “leaks” from the physical implementation of a cryptographic system.
Unlike traditional cryptanalysis, which attacks the mathematical strength of the algorithm itself, a side-channel attack exploits external characteristics or “side channels” of the physical device as it operates.
Attackers can observe various physical phenomena emitted by a computing device to infer sensitive data:
Timing Information: Measuring the precise time it takes for a device to perform operations. If an operation takes slightly longer when processing a “1” bit of a key versus a “0” bit, the key can be reconstructed.
Power Consumption: Analyzing the fluctuations in electrical power drawn by a processor. Different instructions consume varying amounts of power, revealing information about the internal processing steps and key material.
Electromagnetic (EM) Emissions: Measuring the radio waves or other electromagnetic radiation emitted by electronic components. These emissions can carry subtle signals that reveal computational data.
Acoustic (Sound) Cryptanalysis: In some cases, the slight sounds produced by a processor or hardware (e.g., specific capacitor discharge patterns) can reveal information about the data being processed.
Cache Timing Attacks: In a shared computing environment (like cloud computing), an attacker can monitor how their access to shared CPU cache memory is affected by the victim’s cryptographic operations to deduce key material.
Optical Analysis: In laboratory settings, highly sensitive cameras can observe faint light emissions from integrated circuits.
The van Eck phreaking attack, also known as electromagnetic eavesdropping, is a type of side-channel attack that involves capturing and decoding the unintentional electromagnetic (EM) radiation emitted by electronic devices to reconstruct the data being processed. The technique received its name after the Dutch computer scientist Wim van Eck, who published the first unclassified technical analysis and proof-of-concept in 1985.
The US government and NATO have long been aware of this vulnerability (referring to the security standards as TEMPEST). Countermeasures include:
Physical Shielding: Encasing devices and cables in material (like metal housing or a Faraday cage) that blocks or significantly reduces electromagnetic emissions.
TEMPEST-Rated Equipment: Using specially designed, military-grade hardware that meets strict standards for minimal electromagnetic leakage.
Signal Obfuscation: Introducing random noise into the signals being transmitted to make them unintelligible to an eavesdropper.
Maintaining Physical Security: Ensuring that potential attackers cannot get close enough to the sensitive equipment to capture a clear signal.
Fault injection
A fault injection attack is a physical or environmental implementation attack where an adversary deliberately induces computational errors or “faults” within a secure computing system during the execution of sensitive operations, most notably cryptographic processes. The goal is to observe the resulting incorrect outputs or system behavior to deduce sensitive information, such as secret keys or proprietary algorithms.
Common methods for injecting faults include:
Voltage/Power Glitching: Briefly raising or lowering the power supply voltage to cause a logic error in a processor or memory cell.
Clock Glitching: Manipulating the system clock signal frequency or duty cycle to disrupt the normal timing of operations.
Environmental Stress: Exposing the device to extreme temperatures or radiation.
Physical Manipulation: Using strong electromagnetic pulses or focused laser beams directly onto the integrated circuit (IC) to induce errors in specific areas.
Defending against fault injection attacks requires physical security measures, hardware-based encryption, error detection, audits and testing, and robust software/hardware design.
Timing
A timing attack is a type of non-invasive side-channel attack where an attacker measures the precise amount of time taken by a computer system to execute cryptographic operations. The variations in execution time can reveal information about the secret data being processed, most often the encryption key.
The primary defense against timing attacks is to ensure that all sensitive operations execute in a constant amount of time, or conversely, add random delays to hide actual timing, regardless of the secret data being processed.
Man-in-the-Middle (MITM)
A man-in-the-middle (MitM), also referred to as an on-path attack or adversary-in-the-middle (AiTM), is a cyberattack where an attacker secretly inserts themselves between two parties who believe they are communicating directly and securely with each other.
The attacker intercepts all communications, acting as a covert go-between. This position allows them to passively eavesdrop on the conversation (stealing sensitive data) or actively alter, inject, or block messages without the knowledge of either legitimate party.
Examples of On-Path attacks include:
Financial Transaction Fraud: An attacker intercepts an email exchange between a vendor and a customer regarding an invoice. The attacker alters the bank account details in the invoice and redirects the payment to their own account.
Credential Harvesting: An attacker operates a malicious Wi-Fi hotspot at a coffee shop. Users connecting to the network have their traffic monitored, allowing the attacker to capture login credentials for email or banking websites.
Session Hijacking: After a user logs into a secure application, the attacker steals the session cookie or token, allowing them to impersonate the user and access their account without needing the password or a second authentication factor.
Effective defenses involve a combination of strong protocols, vigilant practices, and robust authentication such as using strong encryption (HTTPS/TLS), verifying certificates and MFA.
Pass the hash
A pass-the-hash (PtH) attack is a technique where an attacker steals a user’s password hash (a hashed credential) from a compromised system’s memory or database and reuses that hash to authenticate to other systems or services on the same network without needing to know or crack the actual plaintext password.
The attack exploits the authentication mechanism (primarily the NTLM protocol in Windows environments) where a system uses the hash value for verification instead of the actual password.
Mitigating pass-the-hash attacks requires a defense-in-depth strategy that focuses on preventing initial access, securing credentials, and restricting lateral movement. Migrate from the older NTLM authentication protocol (which is highly vulnerable to PtH attacks) to the more secure Kerberos authentication, use strong, salted password hashing, and MFA.
Kerberos exploitation
Kerberos exploitation refers to a set of advanced cyberattack techniques used to compromise Microsoft Active Directory (AD) environments by manipulating or forging elements of the Kerberos authentication protocol. The primary goal is usually privilege escalation and lateral movement across a network to gain access to sensitive data or systems.
Some common Kerberos exploitation attacks are summarized in the table below.
Ransomware
A ransomware is a type of malware that encrypts a victim’s files, making them inaccessible until a ransom, typically demanded in cryptocurrency, is paid to the attacker.
The core objective of a ransomware attack is to extort money from individuals, businesses, or government organizations by holding their critical data hostage.
The ransomware infects a system, often through phishing emails containing malicious links or attachments, exploited software vulnerabilities (e.g., via Remote Desktop Protocol misconfigurations), or compromised websites (drive-by downloads).
Notable types of ransomware include:
Locker Ransomware: Prevents access to the entire computer system rather than just individual files (e.g., locking the user out of the login screen).
Crypto Ransomware: Encrypts specific files and demands payment for the decryption key (e.g., WannaCry, Ryuk, Conti, LockBit).
Ransomware-as-a-Service (RaaS): A business model where experienced developers license their ransomware code to “affiliates” in exchange for a percentage of the ransom payments.
Defending against ransomware requires a layered security approach:
Regular, Offline Backups: This is the single most important defense. Ensure critical data is regularly backed up to a secure, offline or off-site location that cannot be accessed or encrypted by the ransomware. This allows organizations to restore data without paying the ransom.
Security Software (AV/EDR): Use robust antivirus software and Endpoint Detection and Response (EDR) solutions to detect and block known ransomware variants.
Employee Training: Train employees to recognize and report phishing attempts and suspicious links/attachments, as humans are often the weakest link in the chain.
Software Updates and Patch Management: Keep all operating systems and software updated to patch known security vulnerabilities that ransomware exploits to gain entry.
Principle of Least Privilege: Limit user permissions so that if one account is compromised, the attacker cannot immediately gain access to the entire network or sensitive servers. This includes not providing admin rights to workstation users, and not allowing them to install software.
3.8 - Apply security principles to site and facility design
For the CISSP exam, understanding facility design is important as it forms the foundation of physical security within an organization’s overall security posture. You should focus on how the physical environment is used to control access, mitigate risks, and support security policies.
Key knowledge areas related to facility design for the CISSP exam include:
Secure Facility Plan: A formal document that details the comprehensive security requirements, policies, procedures, and controls (physical, administrative, and technical) necessary to protect a facility, its assets, personnel, and data from unauthorized access, theft, damage, or interference.
Critical Path Analysis (CPA) is a project management technique used to identify the sequence of dependent tasks that determine the shortest possible time required to complete a project. In a security context, it helps identify and prioritize essential activities that, if delayed or compromised, would jeopardize the organization’s mission or the successful implementation of security measures.
Site selection is the evaluation of potential geographic locations for a new facility based on a set of criteria to determine the optimal location for business operations. This process balances operational needs, costs, and risk mitigation, including security considerations.
Site selection is a foundational decision that profoundly impacts the inherent security of a facility and forms the basis of the secure facility plan. A poor choice of location can introduce vulnerabilities that are expensive or impossible to fully mitigate later through physical or technical controls.
Key reasons for its criticality include:
Inherent Risk Assessment: Important considerations include the frequency of natural disasters, and ensuring that structural costs are within budget.
Proximity to high-risk areas (man-made threats): Avoiding locations near chemical plants, power plants, or high-crime areas.
Availability to resources: It is important to have adequate access to fundamental resources such as water, utilities, fuel, medical, fire, and police.
Perimeter and Standoff Zone Design: The site’s physical characteristics, such as terrain and surrounding landscape, influence the ease of establishing a secure perimeter and a proper “standoff zone” (the distance between a potential explosion and the building). A good site layout can use natural barriers (like hills or bodies of water) to enhance security and limit access points (part of “industrial camouflage”).
Facility Design
It’s important to understand organizational requirements for facility design, and to include them in the initial planning (before construction begins).
Crime Prevention Through Environmental Design (CPTED) is a multi-disciplinary approach to deterring criminal behavior and enhancing safety by strategically designing and managing the physical environment.
The theory behind CPTED is that the physical surroundings can directly influence human behavior, making an area either more or less attractive to a potential offender. By leveraging architectural design, landscaping, lighting, and maintenance, CPTED aims to increase the perceived risk for criminals while fostering a sense of ownership and security among legitimate users of the space.
Key principles of CPTED:
Natural Surveillance: Maximize the ability for legitimate users to observe public and private areas. This makes criminals feel they are likely to be seen and reported. This is achieved through strategic placement of windows, effective lighting, and trimming landscaping to remove hiding spots and maintain clear sight lines.
Natural Access Control: Subtly or overtly guide people through a space using physical elements like fences, gates, specific landscaping, and lighting to control access to potential targets and direct foot/vehicular traffic. Natural access control increases the perceived risk for attackers by restricting their movement.
Territorial Reinforcement: Use physical design to create a sense of ownership and clearly define boundaries between public, semi-private, and private spaces. Elements such as clear signage, distinct paving treatments, porches, and well-maintained property send a message that the area is controlled and actively managed, discouraging trespassers. This also includes reinforcement by using access controls including security cameras, controlled access points and systems, and limiting entry points.
Maintenance and Management: A well-maintained property signals that the owners care about the space and are likely to defend it. Neglect (e.g., graffiti, broken windows, overgrown landscaping) suggests indifference and a higher tolerance for criminal activity.
Activity Support: Encouraging legitimate, intended use of a space increases the number of “eyes on the street” (natural surveillance). Designing outdoor spaces or gathering areas that attract positive public use helps deter unwanted behavior.
The Occupational Safety and Health Administration (OSHA) heavily influences facility design by setting mandatory safety and health standards that employers must follow to ensure a hazard-free workplace for their employees. OSHA encourages a proactive approach called “Prevention through Design” (PtD), which integrates safety considerations into the earliest planning and design phases of a project.
OSHA standards dictate numerous facility design elements to mitigate common workplace hazards:
Exit Routes and Emergency Planning: Facilities must be designed with adequate, clearly marked, and unobstructed exit routes for safe and quick evacuation during emergencies like fires or chemical spills. Design requirements specify the number, size, and location of exit doors and paths.
Fall Protection: As falls are a leading cause of workplace injuries, OSHA mandates design features such as permanent anchor points for fall arrest systems, guardrails on elevated platforms, stairs, and ladders, and safe design of facade access systems for building maintenance.
Electrical Safety: Facility design must incorporate specific clearances around electrical equipment (e.g., adequate workspace height and width), appropriate electrical classifications for hazardous areas, and proper grounding and wiring design to prevent shocks and arc flashes.
Ventilation and Air Quality: The design of HVAC systems, exhaust fans, and general ventilation must be sufficient to control exposure to dusts, fumes, vapors, and gases, preventing them from accumulating in harmful quantities in the work atmosphere.
Hazardous Materials Management: For facilities handling highly hazardous chemicals or combustible dusts, design requirements include specific fire suppression measures, firewalls, appropriate building area and height limits, and specialized HVAC designs to safely manage and contain risks.
Site Layout and Material Handling: OSHA influences site layout by requiring adequate space for the safe movement of materials, vehicles, and equipment, which helps prevent bottlenecks and minimizes the crisscrossing of hazards between machinery and personnel.
Ergonomics and Workflow, and Machine Guarding: OSHA requires machines to include guards and safety mechanisms. While not always explicit design codes, OSHA’s General Duty Clause (which requires employers to provide a workplace free from recognized serious hazards) implicitly encourages layouts that minimize ergonomic risks, unnecessary movements, and manual lifting.
The Environmental Protection Agency (EPA) significantly influences facility design through stringent regulations aimed at protecting human health and the environment, as well as by promoting sustainable, “green building” practices. Compliance with EPA regulations is legally required and must be integrated into the planning, design, construction, and operation phases of a facility.
EPA regulations, primarily derived from major environmental statutes, focus on protecting human health and the environment:
Clean Air Act (CAA): Requires the design of proper ventilation systems, air filtration, and emission control technologies to meet air quality standards.
Clean Water Act (CWA): Dictates requirements for managing water usage and preventing contamination of local water bodies.
Resource Conservation and Recovery Act (RCRA): Sets standards for the management, treatment, storage, and disposal of hazardous waste.
Energy and Water Efficiency: Designs are encouraged to optimize energy performance (e.g., efficient HVAC, lighting, renewable energy systems) and conserve water (e.g., high-efficiency plumbing fixtures, reduced irrigation).
Physical Security
You should understand that threats to physical security can be categorized into several primary areas. Recognize these threats, their potential impact, and the appropriate controls (administrative, technical, and physical) to mitigate them.
1. Natural Disasters and Environmental Threats
These threats are often unpredictable and outside human control but can be planned for and mitigated during facility design.
Examples:
Fire: The most common and devastating threat to physical security and assets.
Flood: Damage to equipment, infrastructure, and data integrity.
Extreme Weather: Hurricanes, tornadoes, earthquakes, blizzards, extreme heat/cold.
Key Controls: Site selection, redundant utilities, fire suppression systems, and comprehensive disaster recovery/business continuity plans.
2. Physical Social Engineering
This involves psychological manipulation to trick authorized personnel into granting physical access or revealing sensitive information.
Examples:
Tailgating/Piggybacking: Following an authorized person through a secure entry point without authorization.
Impersonation: Posing as a vendor, a new employee, a fire marshal, or a delivery driver to gain access.
Shoulder Surfing: Observing sensitive information being entered (like PINs or passwords).
Key Controls: Strong access control policies, security awareness training for all employees, and the use of mantraps or turnstiles at secure entry points.
3. Theft and Vandalism
These are intentional acts to steal assets or damage property, leading to financial loss and potential data breaches.
Examples:
Asset Theft: Stealing hardware (laptops, servers, storage media), proprietary documents, or physical media containing sensitive data.
Vandalism: Damaging infrastructure (e.g., cutting cables, defacing property) to disrupt operations.
Key Controls: Layered physical security (fences, locks, alarms), asset tracking and inventory management, surveillance systems (CCTV), and security personnel patrols.
4. Espionage (Corporate/State)
This is the act of covertly obtaining secret or confidential information without the permission of the holder of the information.
Examples:
Installation of Eavesdropping Devices: Planting bugs or hidden cameras in secure meeting rooms.
Data Theft via Physical Media: Stealing USB drives or hard drives containing proprietary information.
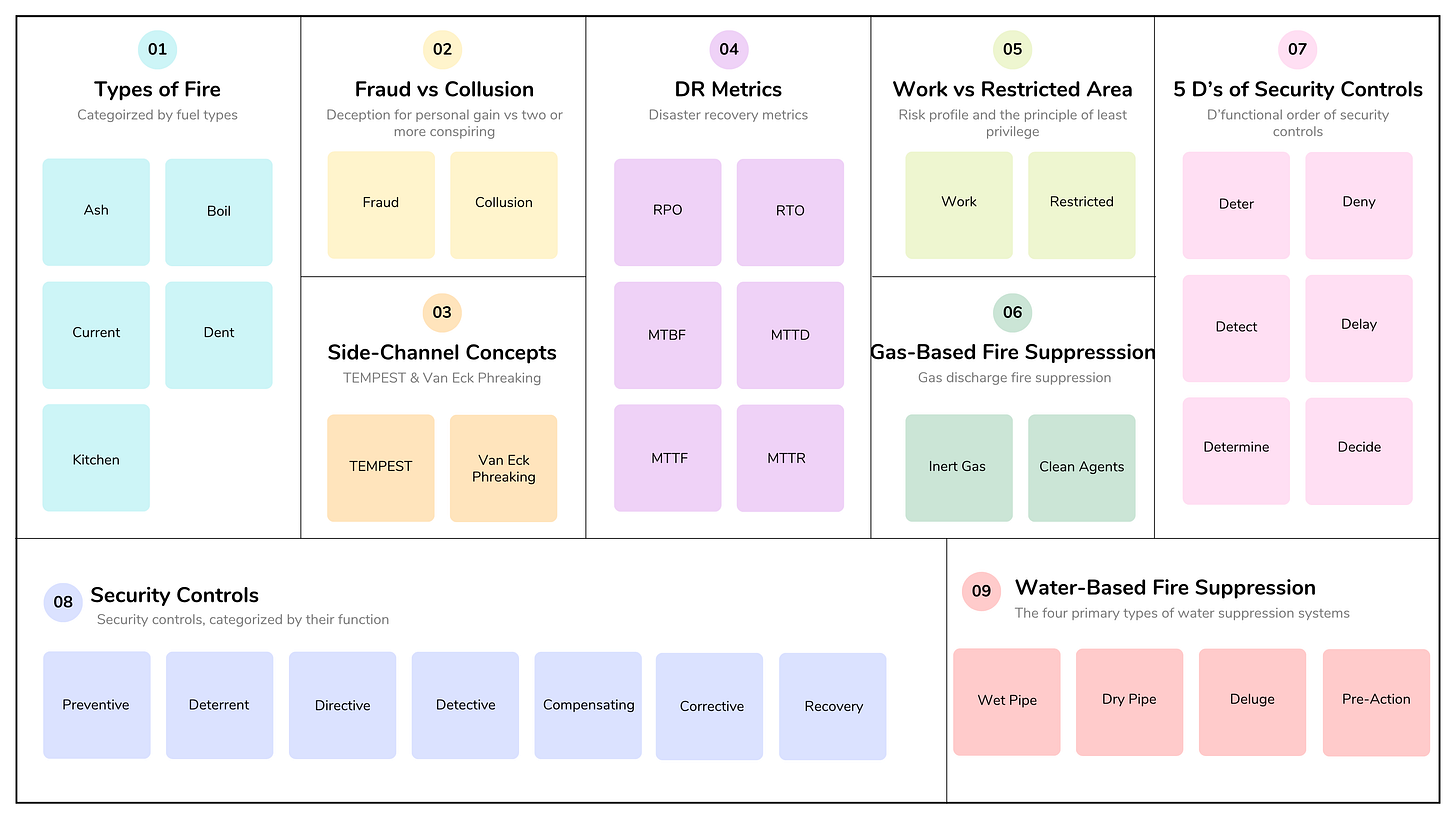
TEMPEST/Van Eck Phreaking: Capturing electromagnetic emissions from devices to reconstruct data (less common but relevant for high-security environments).
Key Controls: Strict visitor control, electronic sweeping of secure areas, proper handling of classified materials, and the use of TEMPEST-approved hardware.
5. Fraud and Collusion
Fraud involves deception for personal gain, while collusion is when two or more individuals conspire to bypass security controls.
Examples:
Fraud: Falsifying time records or expense reports by exploiting weak physical access logs.
Collusion: A security guard working with an employee to facilitate theft or unauthorized access, bypassing individual segregation of duties.
Key Controls: Separation of duties, mandatory vacations, regular audits and reviews of access logs, and anonymous tip lines for reporting suspicious behavior.
6. Operational and Utility Failures
These result from failures in critical infrastructure supporting the facility.
Examples:
Power Outages: Loss of electricity disrupts all operations and security systems.
HVAC Failure: Overheating of server rooms leads to equipment damage and data loss.
Water/Plumbing Failure: Flooding within the building from burst pipes.
Key Controls: Redundant utilities, UPS (Uninterruptible Power Supplies), backup generators, environmental monitoring, and proactive maintenance.
Physical controls are measures used to protect physical assets (facilities, equipment, and data) from threats. They are categorized into three types: administrative, technical (or logical), and physical.
The following is a definition of each category and which controls are typically involved in mitigating the six threat categories discussed previously:
1. Administrative Controls
Administrative controls (also called managerial controls) are organizational policies, procedures, standards, guidelines, and management practices designed to manage risk and govern behavior.
Definition: These are the “rules of engagement” for security.
Examples: Background checks, security awareness training, incident response plans, access control policies, guard procedures, and audit logging reviews.
2. Technical Controls
Technical controls (also called logical controls) are electronic and software-based mechanisms implemented to enforce security policies. While often thought of as digital, in a physical security context, they are the electronic systems that automate or assist in physical security enforcement.
Definition: These are the systems that use technology to protect assets.
Examples: Biometric scanners, CCTV cameras, alarm systems, badge readers, fire suppression systems, and environmental monitoring systems (HVAC, power monitors).
3. Physical Controls
Physical controls (also called operational controls) are tangible items implemented to physically restrict access to resources and assets.
Definition: These are the actual, structural barriers and physical implements that stop an attacker.
Examples: Fences, locks, doors, walls, gates, mantraps, vehicle barriers, and physical security guards.
The seven types of security controls, categorized by their function or goal within a security framework, are:
1. Preventive Controls
Preventive controls are designed to stop a security incident from happening in the first place. They are proactive measures.
Goal: Avoid the incident entirely.
Examples: Firewalls, encryption, user access controls (passwords), physical locks on doors, and security awareness training.
2. Deterrent Controls
Deterrent controls are intended to discourage potential attackers from attempting to violate security policies or procedures. They aim to make the attack seem like too much work or too risky.
Goal: Discourage the threat agent.
Examples: Guard dogs, bright lights, CCTV cameras (visible ones), warning signs, and visible security personnel.
3. Directive Controls
Directive controls are administrative mechanisms that mandate or guide desired actions and behaviors of individuals within the organization.
Goal: Define, confine, or control behavior to comply with policy.
Examples: Security policies, procedures, regulations, laws, and mandatory background checks.
4. Detective Controls
Detective controls are designed to identify, discover, or detect an incident that is either currently occurring or has already occurred. They do not prevent or correct an incident but provide notice of its existence.
Goal: Identify incidents after they happen.
Examples: Audits, log monitoring, intrusion detection systems (IDS), honey pots, CCTV recordings, physical alarms, and mandatory vacation policies (to detect fraud).
5. Compensating Controls
Compensating controls are alternative measures used to satisfy a specific security requirement when the primary or intended control cannot be fully implemented due to business constraints, technical limitations, or cost.
Goal: Provide an alternative way to meet a requirement.
Examples: Using enhanced monitoring for an older application that cannot be patched, or using an additional password complexity rule because multi-factor authentication cannot be implemented yet.
6. Corrective Controls
Corrective controls are intended to minimize the impact of a security incident after it has occurred and restore the system or asset to its previous secure state.
Goal: Return systems to normal, or minimize damage and repair the situation.
Examples: Patching a vulnerability after it has been exploited, restoring data from backups, using anti-virus software to quarantine and remove malware, and disciplinary actions for policy violations.
7. Recovery Controls
Recovery controls are extensions of corrective controls that focus on the comprehensive process of restoring business operations and systems after a major incident or disaster.
Goal: Restore full business operations and functionality.
Examples: Disaster recovery plans (DRP), business continuity plans (BCP), and the use of off-site backup facilities.
The functional order of security controls describes the typical sequence of events when defending against a physical security threat. The exact sequence can vary slightly depending on the specific model used, but a common and comprehensive framework is:
Deter: Discourage an attacker from attempting a security breach.
Deny: If deterence fails, prevent unauthorized entry or access to assets.
Detect: If deny fails, identify that a security breach attempt has occurred or is occurring.
Delay: Slow down the progress of an attacker.
Determine: Assess the nature and scope of the attack.
Decide: Choose the appropriate response strategy based on the determined attack scenario.
Functional order: Deter→Deny→Detect→Delay→Determine→Decide
Disaster Recovery metrics
Understanding disaster recovery metrics is essential for planning, designing, and testing business continuity and disaster recovery plans. These metrics help define acceptable downtime, data loss, and recovery capabilities.
Here is a summary of the key metrics you should know:
KPIs for physical security
Common Key Performance Indicators (KPIs) for physical security help organizations measure the effectiveness of their security program, demonstrate value to management, and identify areas for improvement.
KPIs can be broadly categorized into incident management, operations efficiency, and compliance.
Incident Management & Response KPIs
These metrics focus on how effectively and quickly the security team handles actual or attempted incidents. Examples include:
Number of Security Incidents/Breaches: A raw count of unauthorized access incidents (e.g., forced entry, tailgating, fence jumping), thefts, or security policy violations. The goal is often to reduce this number over time.
Incident Response Time: The average time from when an alarm or alert is triggered until security personnel arrive on the scene or begin containment efforts. A shorter time indicates greater efficiency.
Operational Efficiency KPIs
These metrics measure the performance and reliability of the tools and personnel involved in day-to-day security operations. Examples include:
Access Control Violations: The frequency of attempts to access areas where individuals are not authorized. This indicates the effectiveness of access controls and user awareness.
Security Equipment Uptime: The percentage of time that critical security systems (CCTV, access control units, alarms) are fully operational. High uptime ensures continuous protection.
Compliance & Awareness KPIs
These metrics ensure that the security program aligns with internal policies, external regulations, and that employees are adequately trained. Examples include:
Training and Certification Compliance: The percentage of security personnel and general staff who have completed required security awareness training or certifications within the deadline.
Security Audit Success Rate: The percentage of compliance audits (internal or external) that the facility passes, indicating adherence to regulatory standards (e.g., specific industry standards).
By tracking these KPIs, security managers can make data-driven decisions to justify investments, prioritize resources, and continuously improve the overall security posture of the facility.
3.9 - Design site and facility security controls
Wiring closets/intermediate distribution facilities
Wiring closets and Intermediate Distribution Facilities (IDFs) are essential infrastructure spaces within a building’s network architecture.
Wiring Closet: A centralized location where telecommunications equipment, cables, and connections terminate. This type of room might house patch panels and network equipment, making physical security paramount.
Intermediate Distribution Facility (IDF): This term refers specifically to a secondary wiring closet used to connect telecommunications circuits from an MDF (Main Distribution Facility, typically a main data center or core wiring closet) to end-user equipment in remote parts of a building or campus.
These areas are critical for physical security because they house the central nervous system of the organization’s network and communication systems. A breach in these locations can have a disproportionately large impact on overall security.
The point here is to understand that there is no security without physical security.
Due to their importance, these facilities require strong physical security controls:
Physical Locks and Access Control: Doors must be securely locked with strong physical locks or, ideally, electronic access control systems (badge readers) that log all entries.
Restricted Access: Access should be limited strictly to authorized IT and facilities personnel based on the principle of least privilege.
Surveillance and Logging: Monitor and log access to wiring closets and IDFs. Use CCTV cameras to monitor access and internal activities within the space. Implement door alarms and potentially motion sensors to detect unauthorized access attempts.
Organization and Management: Keep the equipment, area, and wiring organized and secure cabling via appropriate management.
Environmental Monitoring: Monitor temperature, humidity, and power status to prevent operational failures or detection of tampering (e.g., unplugging power).
Server rooms/data centers
Securing server rooms and data centers is of paramount importance because these facilities house an organization’s most critical and sensitive assets: data, processing power, and core network infrastructure. A breach here can lead to devastating consequences, including regulatory fines, reputational damage, significant financial loss, legal liability, and complete operational shutdown.
A defense-in-depth strategy is essential, layering administrative, technical, and physical controls to protect these critical assets:
Physical Controls (Structural and Barriers) such as reinforced doors, access control vestibule (AKA mantrap) to prevent tailgaiting, and locks on server cabinets.
Technical Controls such as CCTV, environmental monitoring such as sensors for temperature, humidity, water leakage (under raised floors), smoke/fire, and power fluctuations with automated alert systems, and redundant power.
Administrative Controls such as least privilege access (only for required personnel, limited by time and area), access log reviews and audits, and security awareness training.
Media storage facilities
Media access facilities are secure areas designed specifically for storing, handling, accessing, and disposing of various data storage media, such as backup tapes, optical disks, hard drives, USB drives, and microfilm/microfiche. These facilities serve as libraries or archives where digital and physical records are managed when not actively in use on a computer system.
The importance of securing these facilities lies in the sensitivity of the data stored on the media. A single backup can contain the entirety of an organization’s intellectual property, customer data, and internal communications.
Security for media access facilities requires a layered approach, integrating physical, technical, and administrative controls:
Physical Controls: store media in a designated locked and secure location, maintaining stable temperature and humidity levels, and protected with fire suppression systems.
Technical Controls: use electronic access control (badge readers, biometrics) with detailed logging of entries and exits, monitor all access points and internal areas of the facility 24/7 with cameras, and use sensors to detect temperature spikes, humidity changes, smoke, and water leakage.
Administrative Controls: use a strict access policy, a clear administrative policy for labeling media, use secure transit procedures with chain-of-custody documentation, implement media sanitization and disposal policies, and regularly audit the facilities and media library.
Evidence storage
Evidence storage refers to secure facilities or designated locations used to physically or digitally store items collected during an investigation, audit, or incident response. This can range from digital media (hard drives, USB sticks, mobile phones) to physical documents, network logs, and physical artifacts potentially related to a crime or breach.
A chain of custody proves the integrity of a piece of evidence, and is the documentation and tracking of that evidence from collection through court use.
The critical requirement for evidence storage is maintaining an unbroken chain of custody and ensuring the integrity of the evidence so that it is admissible in a legal or disciplinary proceeding.
The primary importance is legal admissibility. If evidence is handled improperly, tampered with, or its integrity cannot be verified, it may be dismissed in court, potentially jeopardizing the entire case. Therefore, security controls for evidence storage prioritize documentation, limited access, and integrity verification.
Restricted and work area security
Work Area: Refers to general office spaces or labs used for daily work. While access is typically limited to authorized employees, the controls are less stringent than in restricted areas, allowing for normal workflow. Examples include cubicle farms, general meeting rooms, and common break areas.
Restricted Area: Refers to any highly sensitive area where access is tightly controlled and limited only to personnel with a specific, justified “need-to-know” or “need-to-access” clearance. These areas house critical assets, sensitive data, or essential infrastructure. Examples include data centers, server rooms, evidence storage facilities, executive suites, and R&D labs.
Security for restricted and work areas involves applying a layered, risk-based approach to differentiate access levels within a facility, moving from public areas to highly sensitive ones.
The primary difference between work and restricted areas lies in the risk profile and the principle of least privilege: restricted areas assume a higher potential for impact if breached and thus require stricter controls than general work areas.
Security considerations involve a defense-in-depth strategy, layering administrative, technical, and physical controls appropriate to the sensitivity of the area:
Identification and Authentication: Work Areas often use simple badge readers, key access, or standard keypads. Restricted Areas require stronger, often multi-factor authentication (MFA). This might include a badge plus a PIN, or a badge plus a biometric scan (fingerprint, iris, or facial recognition).
Architectural and Physical Controls: The facility design should physically separate restricted areas from general work areas and public spaces. The use of robust walls (floor-to-ceiling), solid doors, and minimal windows helps enforce this separation. Highly restricted areas should use access control vestibules (mantraps) to prevent tailgating and piggybacking, allowing only one authenticated person to enter the secure zone at a time.
Monitoring and Surveillance: Strategic camera placement and monitoring in restricted areas, motion sensors, door contact alarms, intrusion detection, and auditing and logging for entry and exit attempts in restricted areas.
Administrative and Operational Controls: Policies clearly defining access levels and sanctions for violations, clean desk and clear screen policies, and secure workstations and equipment to prevent unauthorized access and physical theft.
Utilities and Heating, Ventilation, and Air Conditioning (HVAC)
Utilities and Heating, Ventilation, and Air Conditioning (HVAC) systems are the critical life support infrastructure of any modern facility, providing the power, connectivity, climate control, and water necessary for operations.
Failures or attacks targeting utilities and HVAC systems can lead to significant operational disruptions, equipment damage, data loss, and safety hazards.
Environmental issues (e.g., natural disasters, man-made)
Environmental issues pose significant threats to site and facility security, potentially causing operational downtime, data loss, and safety hazards. These threats are broadly categorized as natural disasters and man-made issues.
Natural disasters such as floods/earthquakes/extreme weather: Can cause physical damage to the building, infrastructure, and IT equipment and loss of utilities (power, water, network), leading to complete operational failure and data loss if backups are inaccessible or destroyed.
Man-made issues such as fires/spills/infrastructure failure: Fires can destroy assets and threaten lives. Chemical spills can contaminate the environment. Utility failures (e.g., power grid outages) disrupt security systems and business operations.
Mitigation strategies focus on proactive planning, redundant systems, and robust physical controls:
Implement redundant systems for all critical utilities including power (UPS and backup generators), HVAC (backup cooling systems and environmental monitoring), and networking systems (multiple diverse network paths and carriers).
Physical protection including fire suppression, and containment strategies.
Planning and policies including implementing and regularly testing business continuity and disaster recovery (BC/DR) plans, regular maintenance on systems and controls, and off-site backups.
Fire prevention, detection, and suppression
Fires are categorized based on the type of fuel they consume. Different agents are required to effectively suppress them, and using the wrong agent (e.g., water on an electrical fire) can be dangerous.
The three categories of fire detection systems are defined by the physical characteristics of a fire they are designed to sense: smoke sensing, flame sensing, and heat sensing.
The four primary types of water suppression systems, are chosen based on the environment’s temperature and the need to prevent accidental water discharge.
Wet Pipe: This is the most common and reliable type of system. The pipes are filled with water under pressure at all times. Water is immediately discharged from a sprinkler head triggered by a fire’s heat.
Dry Pipe: The pipes are filled with pressurized air or nitrogen instead of water. A main valve holds the water supply back. When a sprinkler head activates, the air pressure in the pipe drops, which triggers the main valve to open, allowing water to fill the pipes and flow to the activated heads. Often used where water in pipes may freeze.
Deluge Systems: In a deluge system, all sprinkler heads attached to the piping system are open and do not have individual heat-sensitive elements. The pipes are empty until a separate fire detection system is triggered.
Pre-Action Systems: These systems are a hybrid designed for highly water-sensitive areas (e.g., data centers, museums, libraries) where accidental water discharge would cause significant damage. The pipes contain pressurized air, and a pre-action valve holds back the water. A two-step process to prevent accidental activation: first, a separate fire detection event must occur, and second, a sprinkler head must also be activated by heat.
Non-water suppression:
Gas discharge: Fire suppression systems release inert gases or specialized chemical agents into an enclosed area to extinguish a fire, typically without using water. These systems are usually more effective, because they work by removing oxygen (one of elements of the Fire Triangle — heat, fuel, oxygen). However, these systems shouldn’t be used in spaces occupied by people.
Inert Gases (e.g., Argonite, Inergen, Nitrogen) reduce the oxygen concentration in the room to a level where combustion cannot be sustained.
Clean Agents (e.g., FM-200, Novec 1230) are synthetic chemical compounds that chemically interfere with the combustion process and absorb heat rapidly.
They are widely used in critical environments like data centers, server rooms, and museums because they suppress fires quickly, leave no residue, and minimize damage to sensitive electronic equipment or valuable artifacts.
Note that Halon is an extremely effective fire suppression agent, but was banned from production use due to its severe ozone-depleting potential.
Power (e.g., redundant, backup)
A UPS (Uninterruptible Power Supply) and a generator are both power backup solutions used to ensure continuous operation of critical systems during a main power outage, but they serve different primary goals and operational purposes.
A UPS is a device that contains a battery backup system, surge protection, and power conditioning circuitry. It is placed between the main power source and the equipment it protects (e.g., servers, security systems, computers).
A UPS provides a short window of time (usually minutes) to gracefully shut down equipment or transition to a secondary power source, such as a generator.
A generator converts mechanical energy (usually from burning fuel like diesel, natural gas, or propane) into electrical energy. It’s goal is to provide long-term, sustained power during extended outages.
Commercial power problems are variations in the quality, voltage, or frequency of the electricity supplied to a facility. They are categorized by their nature, duration, and causes:
The most common solutions for these power problems include the use of Uninterruptible Power Supplies (UPSs) for short-term protection and clean power conditioning, and generators for long-term outages.
3.10 - Manage the information system lifecycle
The Information System Lifecycle describes the major stages of an information system’s existence, from its initial conception to its final retirement. Understanding this lifecycle is important for applying security controls at the appropriate time and ensuring that security is a continuous, integrated process rather than an afterthought.
Typical stages of the Information System Lifecycle:
Stakeholders needs and requirements
Stakeholder Needs and Requirements: The initial phase of any project involves figuring out who has a stake in the outcome and what they actually need and expect. This means carefully analyzing requirements from end-users, managers, regulators, and anyone else involved with the system.
Requirements analysis
Requirements Analysis: This phase is about a deep dive into all the requirements. This includes defining what the system must do (functional requirements) and how it must perform (nonfunctional requirements), while also considering any limitations and making sure everything matches the company’s goals.
Architectural design
Architectural Design: In this phase, you build the system’s master blueprint. This plan defines the overall structure, all the different parts, how data moves through the system, and how the parts connect to each other.
Development /implementation
Development/Implementation: This phase is where the system is actually built. Developers write the code, set up the hardware, and connect all the different parts to make the system functional.
Integration
Integration: This phase involves combining all the pieces of the system to make sure they work together smoothly. The main goal is to ensure all individual elements function as a single, unified system.
Verification and validation
Verification and Validation: This phase is about making sure the system actually works correctly and meets the original needs. Verification checks if all the parts were built right. Validation checks if the finished system serves its overall purpose.
Transition/deployment
Transition/Deployment: This phase is when the system is released for use. It involves moving the finished system from the testing environment into the live, operational setting and making it available to the people who need it.
Operations and maintenance/sustainment
Operations and Maintenance/Sustainment: In this phase, the system is live and actively used. This involves the day-to-day management, monitoring, and support needed to keep it running correctly. Ongoing maintenance, like fixing issues and applying updates, ensures the system remains functional and secure for the long term.
Retirement/disposal
Retirement/Disposal: When a system is no longer needed, it’s carefully shut down and retired. This phase includes securely getting rid of the data, following compliance, and deciding how to replace the system or what to do next.
If you’re on the CISSP journey, keep studying and connecting the dots, and let me know if you have any questions about this domain.