Understanding CISSP Domain 7, Security Operations - Part 3
Security Operations is the practical application of security concepts to identify, investigate, and mitigate risks throughout a business’s daily activities and operational lifecycle.
Part 1 covered application of important concepts, including investigations, evidence collection, logging and monitoring, threat intelligence, and configuration management.
In Part 2, we continued exploring areas such as resource protection, incident response, and detection and preventive technologies.
In Part 3, we’ll look at vulnerability and patch management, change management, and disaster recovery plans, processes, and testing.
Let’s dive into the domain and cover the material by following the ISC2 exam outline.
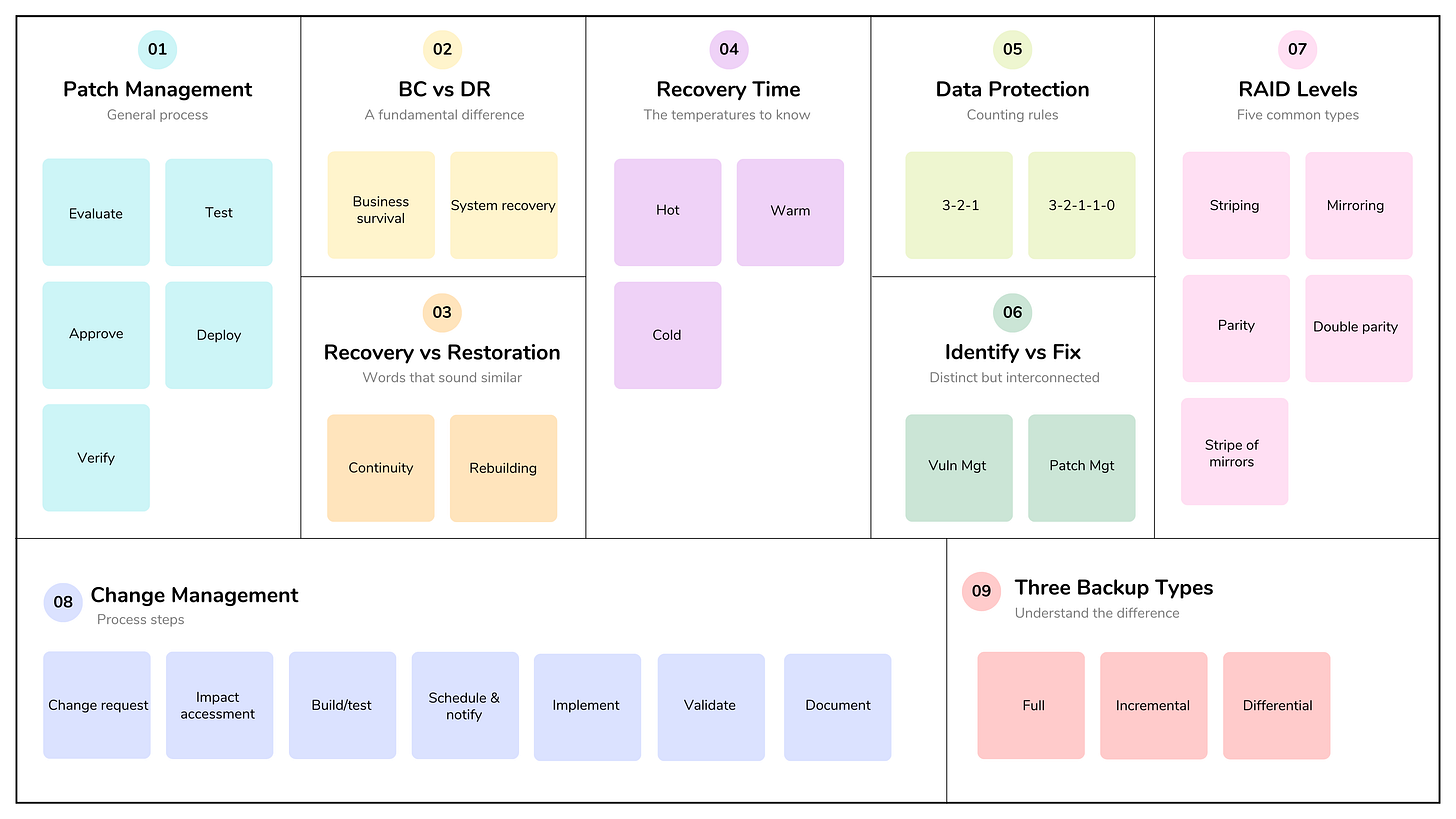
7.8 - Implement and support patch and vulnerability management
Patch management and vulnerability management are distinct but interconnected cybersecurity processes. While vulnerability management identifies the “cracks” in a system, patch management provides the “repair.” Patch and vulnerability management processes work together to help protect against emerging threats. Patch management ensures that fixes are applied to systems, and vulnerability management helps verify that systems are not vulnerable.
Vulnerability Management: A broad, continuous, and strategic lifecycle used to identify, assess, and prioritize security weaknesses, including software flaws, misconfigurations, and weak authentication, across an organization’s entire IT footprint. Like other areas of cybersecurity, this lifecycle increasingly leverages AI to filter through the thousands of newly published vulnerabilities every year.
Patch Management: A tactical, operational process focused specifically on identifying, testing, and deploying software updates or patches provided by vendors to fix known bugs and security holes. Change and configuration management are often used to make the patch management process work effectively.
Patch management is often viewed as a subset of the broader change and configuration management disciplines. While they overlap, each serves a distinct role in ensuring that security updates are applied safely and predictably.
Configuration management provides the foundation for patching by maintaining a known, secure baseline of all systems, while change management acts as governance for patching, ensuring that updates don't cause operational outages.
You should be familiar with the patch management process as follows: