Understanding CISSP Domain 7, Security Operations - Part 2
Security Operations is the practical application of security concepts to identify, investigate, and mitigate risks throughout a business's daily activities and operational lifecycle.
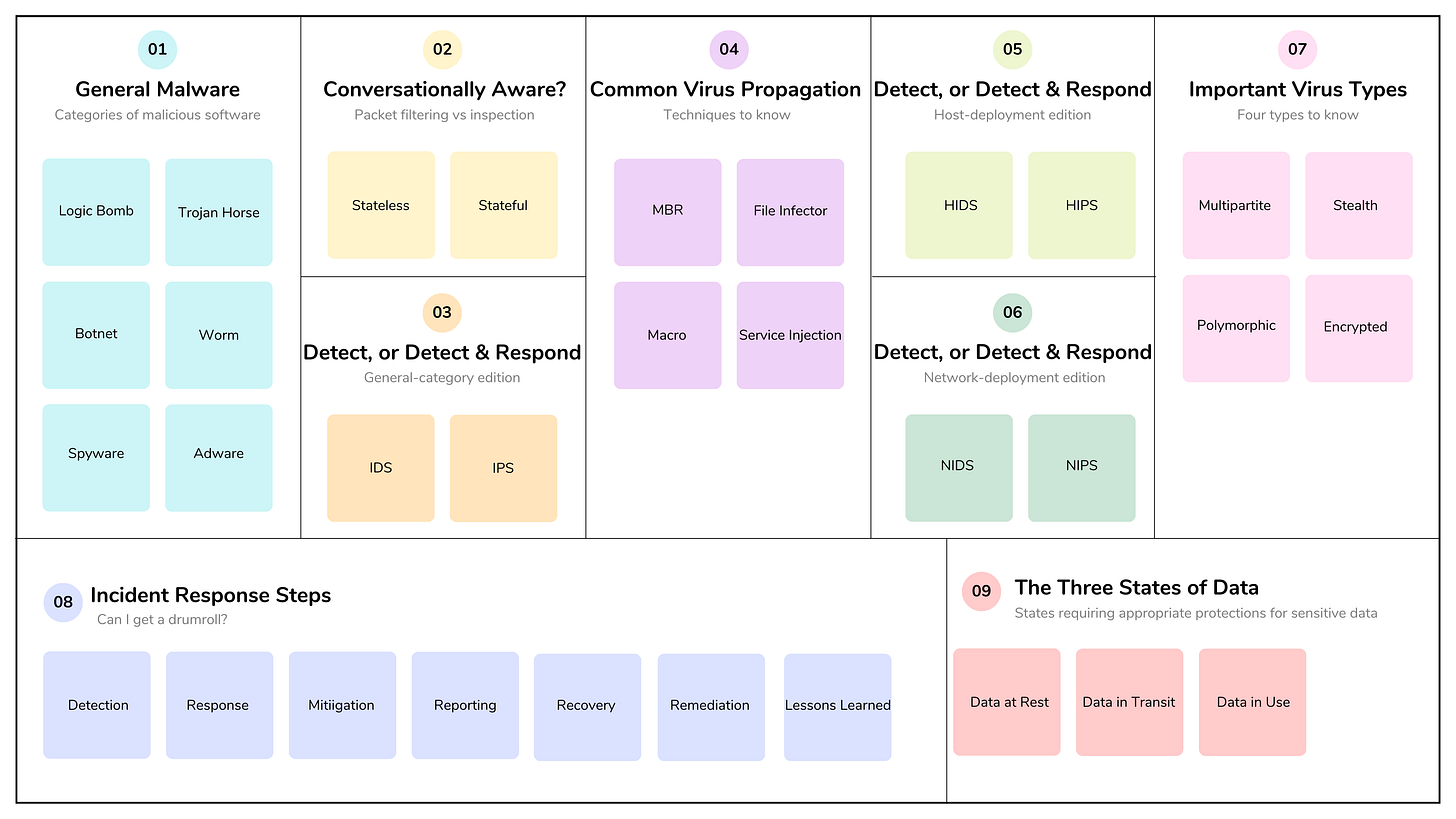
In Part 1, we covered the basics, including the different types of investigations, evidence collection, logging and monitoring, threat intelligence, configuration management, and a few core security operations concepts.
In Part 2, we continue exploring the application of resource protections, incident response, and detection and preventive technologies. Let’s dive into the domain and cover the material by following the ISC2 exam outline.
7.5 - Apply resource protection
Organizations need to protect sensitive data and systems at every stage of their lifecycle, from secure provisioning and storage to proper disposal when assets are no longer needed.
Media management
Media management includes the security controls and techniques needed to protect media and stored data. Organizations use a wide variety of storage media, requiring appropriate policies and security controls to maintain confidentiality, integrity, and availability.
Organizations use a variety of media types that require protection to prevent data breaches, tampering, and loss. Security frameworks and best practices emphasize a mix of physical and digital controls to effectively manage these risks.