Understanding CISSP Domain 5: Identity and Access Management (IAM) - Part 2
Identity and Access Management covers the concepts, policies, processes, and technologies that ensure the right people and things have appropriate access to the right resources at the right time.
In Part 1, we covered logical and physical access controls across general categories such as information, systems, devices, applications, and services. We discussed AAA services, the five essential pillars of comprehensive access control, credential management systems, SSO, and FIM.
In Part 2, we continue exploring the implementation and management of authentication and authorization systems, as well as the identity and access provisioning lifecycle. Let’s dive into the domain and cover the material by continuing to follow the ISC2 exam outline.
5.4 - Implement and manage authorization mechanisms
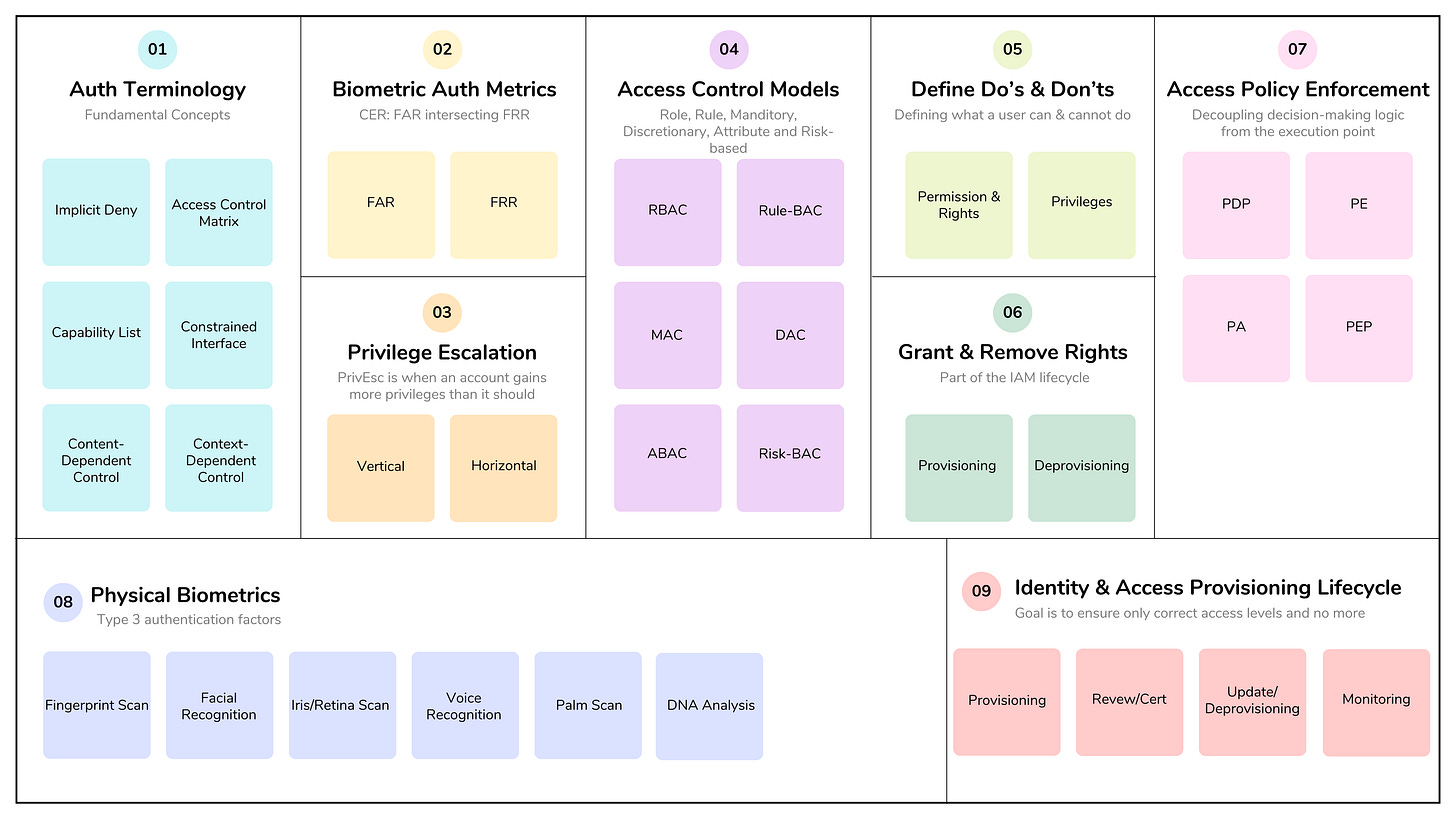
In the context of implementing and managing authorization mechanisms within Identity and Access Management (IAM), the terms permissions, rights, and privileges are often used interchangeably, but they typically have subtly different meanings depending on the specific operating system or vendor being discussed.
Generally speaking, these terms all define what a user is allowed to do within a system, rather than who the user is. They are the granular building blocks of an authorization model (e.g., Role-Based or Attribute-Based Access Control).