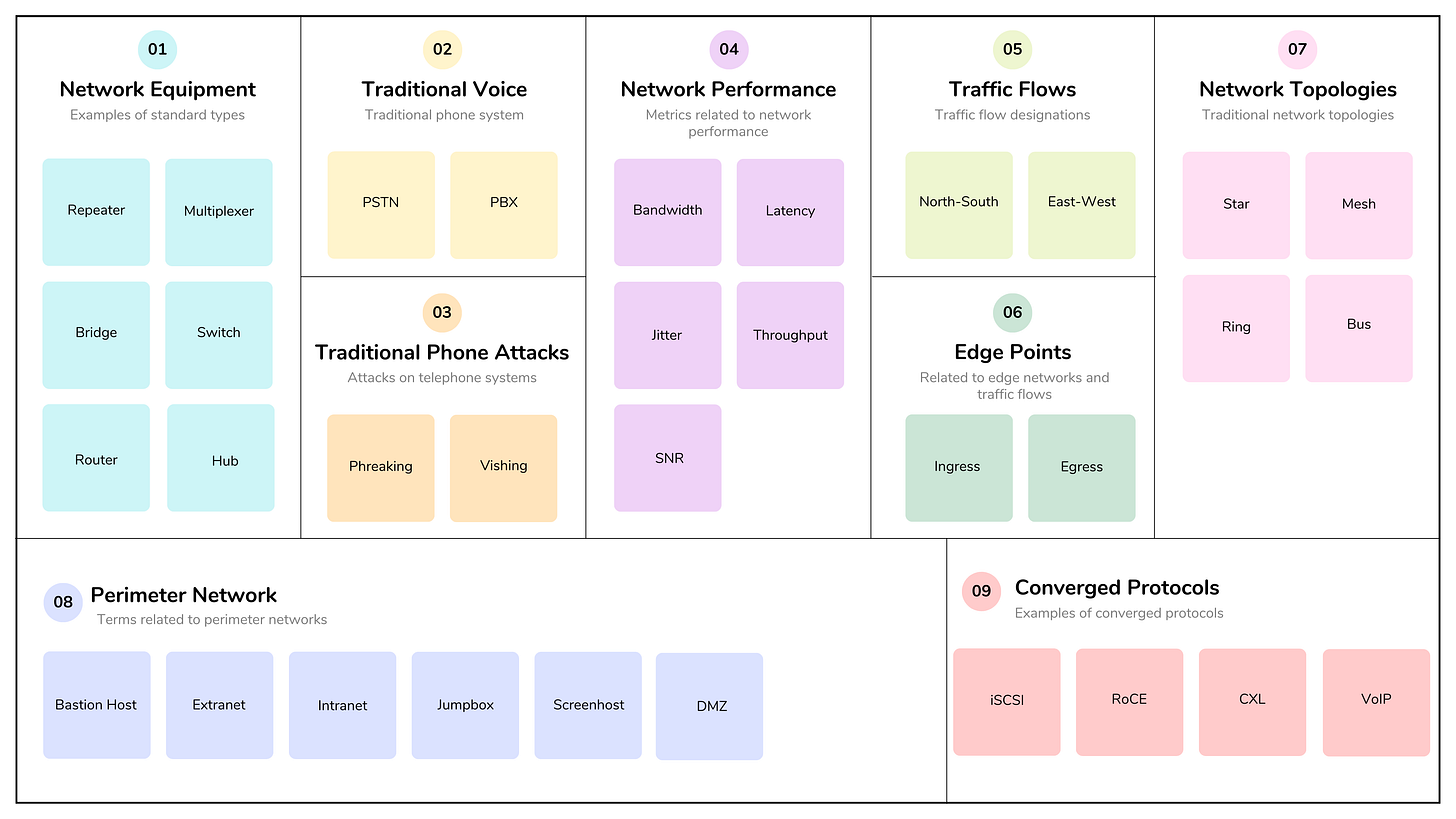
Understanding CISSP Domain 4: Communication and Network Security - Part 2
Communication and Network Security covers the design and protection of enterprise network architecture, secure communication channels, and the technologies used to move and protect data across those networks.
In Part 1, we covered the application of secure design principles in network architectures, including the OSI and TCP/IP models, IPv4 and IPv6, authentication and VPN protocols, and network attacks. In Part 2, we continue with multilayer protocols, network topologies and technologies. Let’s dive into the domain and cover the material by continuing to follow the ISC2 exam outline.
4.1 Apply secure design principles in network architectures
Implications of multilayer protocols
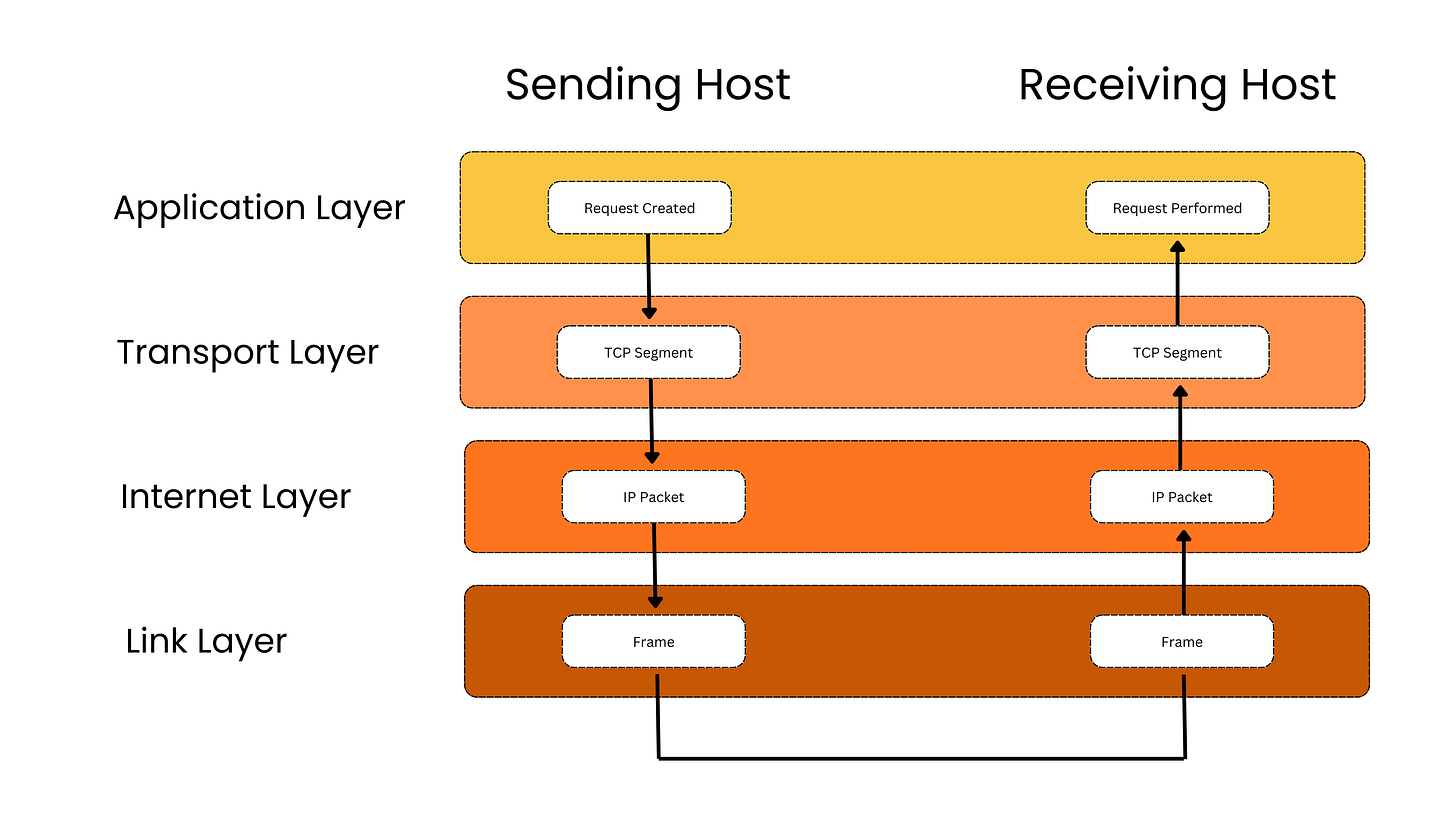
The TCP/IP suite uses a multilayer protocol design that allows data to be encapsulated at different layers. This means that protocols at higher layers can be wrapped or nested within lower-layer protocols. For instance, HTTP can be encapsulated within TCP, which is then encapsulated in IP, and finally in Ethernet. The entire process is reversed (the data is de-encapsulated, or decapsulated) when it is returned to the requester.
For example, here are the high-level steps for a user sending and receiving a web page request:
The user sends a browser page request (from sender to receiver):
Application Layer: Prepares user data using a protocol like HTTP.
Transport Layer (TCP/UDP): Breaks data into segments and ensures reliable (TCP) or fast (UDP) delivery. For an HTTP request, TCP is used.
Internet Layer (IP): Adds IP addresses and decides the best route for each packet.
Link Layer (Network Access): Converts packets into frames and sends them over the physical network.
The user’s browser page request is received (at the destination):
Link Layer: Receives bits from the network and rebuilds frames to pass to the next layer.
Internet Layer: Checks the IP address, removes the IP header, and forwards data to the Transport Layer.
Transport Layer: Reassembles segments, checks for errors, and ensures data is complete.
Application Layer: Delivers the final data to the correct application (e.g., displays a web page in the browser).
Multilayer protocols, such as the TCP/IP suite, offer network advantages such as flexibility, robust management, and widespread compatibility:
Modularity: A modular design means that protocols can be used or swapped out at different layers without disrupting the functionality of other layers.
Flexibility: The layered architecture enables networks to scale from very small (e.g., a home network) to global.
Security: Encryption can be used a various layers based on requirements, providing better data protection.
Interoperability: Because the TCP/IP suite is an open standard that is universally adopted, it ensures seamless communication between diverse hardware and software from different vendors, operating systems, and network types.
TCP/IP provides some operational challenges and inherent security vulnerabilities, which are important considerations:
Inherently Insecure Design: IPv4 was designed for connectivity and resilience rather than security, and security measures need to be applied to provide better safety (e.g., IPsec).
Boundary Violations: A trust boundary is a conceptual line in a system’s architecture that separates areas with different levels of security and privilege. Data on one side is considered untrusted, and data on the other side is considered trustworthy. A violation occurs when unvalidated, untrusted data crosses this boundary and is used in a context where it is assumed to be safe. In the context of TCP/IP, a boundary violation refers to data originating from an untrusted source (such as a user or the internet) mistakenly being treated as trustworthy by higher layers or within a secure part of the system.
Filter Bypass: Attackers can exploit the interactions between layers to evade security controls. For example, they might use data tunneling to wrap malicious traffic within what appears to be harmless protocol data, thereby bypassing firewalls or intrusion detection systems (IDS).
Covert Channels: Related to filter bypass, the complexity of layer interactions can inadvertently create “covert channels” where unauthorized parties can secretly communicate or exfiltrate data by manipulating protocol fields that are not typically monitored by security tools.