Understanding CISSP Domain 8, Software Development Security - Part 1
CISSP Domain 8 focuses on securing software throughout the development lifecycle, from design and coding to testing, deployment, and maintenance. In Part 1, we’ll cover how to develop software securely from the very beginning of a project, using secure design principles, development practices, and testing methods to reduce risk in enterprise applications.
Here is a breakdown of the topics in this domain:
Security in the software development life cycle (SDLC): Integrating security tasks into various methodologies such as Agile, Waterfall, Spiral, and DevSecOps, and understanding how maturity models and change management fit in.
Security controls in development ecosystems: Identifying and applying controls for programming languages, libraries, toolsets, and CI/CD pipelines. Utilizing various assessment methods to verify security, including SAST, DAST, and SCA.
Software Security Effectiveness: Using auditing, logging, risk analysis, and mitigation.
Acquired Software Security: Assessing the security impact of Commercial Off-the-Shelf (COTS), open-source, third-party, and cloud-based software before integration into the organization.
Secure Coding Guidelines: Identifying and addressing security weaknesses, applying standards to improve areas such as secure coding practices and API security.
Let’s dive into the domain and cover the material by following the ISC2 exam outline.
8.1 - Understand and integrate security in the Software Development Life Cycle (SDLC)
The software development life cycle (SDLC) is the process of designing, creating, testing, and deploying software. From a security perspective, application development has become more complicated over the last few years, even as the introduction of AI-assisted coding has increased developer output. Incorporating guardrails and boundaries, staying on top of the latest changes, and ensuring the security of the application environment in production continue to be challenging.
From the CISSP perspective, SDLC terminology varies across models and publications, but what is most important is understanding the fundamental principles of how the process works.
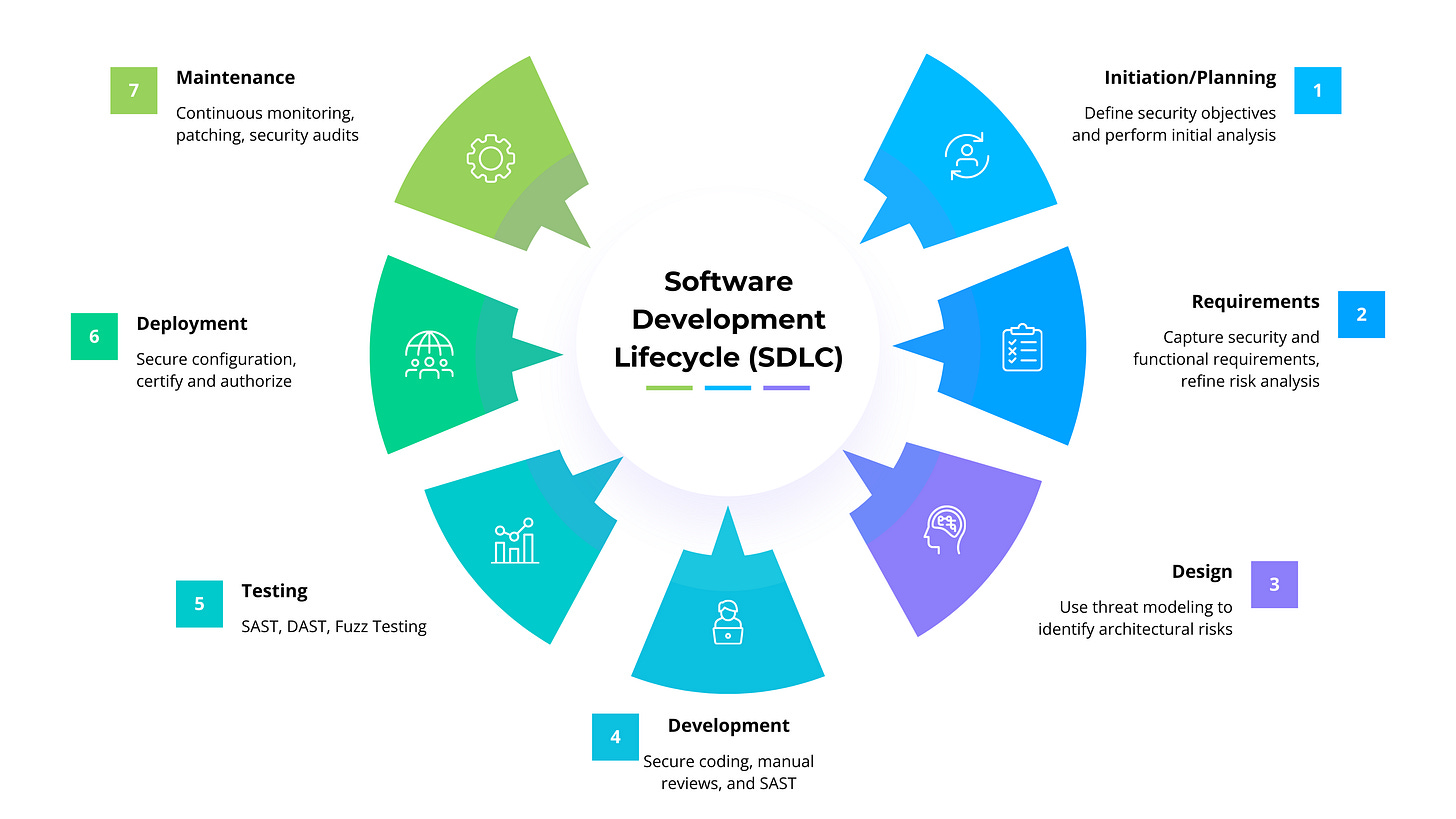
One of the most important aspects of the SDLC is that security must be incorporated at every phase. While terminology may differ by methodology (such as Waterfall or Agile), the core phases and their associated security activities generally include:
Initiation/Planning: Define security objectives and perform initial risk assessments.
Requirements Definition: During this phase, security requirements are captured alongside functional requirements, and risk analysis is refined.
System Design: Threat modeling is used to identify architectural risks early in the design phase, before coding begins.
Development/Coding: Apply secure coding standards, conduct manual code reviews, and use static application security testing (SAST) to identify issues early.
Testing/Evaluation: Perform dynamic application security testing (DAST), fuzz testing, and additional SAST to validate security before release.
Deployment/Release: Ensure secure configuration, complete final certification and authorization activities to confirm the system is approved for production use.
Maintenance/Operations: Continuously monitor for emerging threats, apply patches and updates, and perform regular security audits.