Understanding CISSP Domain 8, Software Development Security - Part 2
CISSP Domain 8 focuses on securing software throughout the development lifecycle, from design and coding to testing, deployment, and maintenance. In Part 1, we covered how to develop software securely from the very beginning of a project, using secure design principles, development practices, and testing methods to reduce risk in enterprise applications.
In Part 2, we’ll look at software security effectiveness, including auditing and logging, risk analysis and mitigation, identifying and addressing security weaknesses, and improving API security and coding practices.
Let’s jump into the domain and cover the material by following the ISC2 exam outline.
8.3 - Assess the effectiveness of software security
Assessing software security through auditing, logging, risk analysis, and mitigation is important for shifting from a reactive to a proactive defense strategy. Together, these practices provide the visibility and actionable insights needed to safeguard critical assets.
Auditing and logging of changes
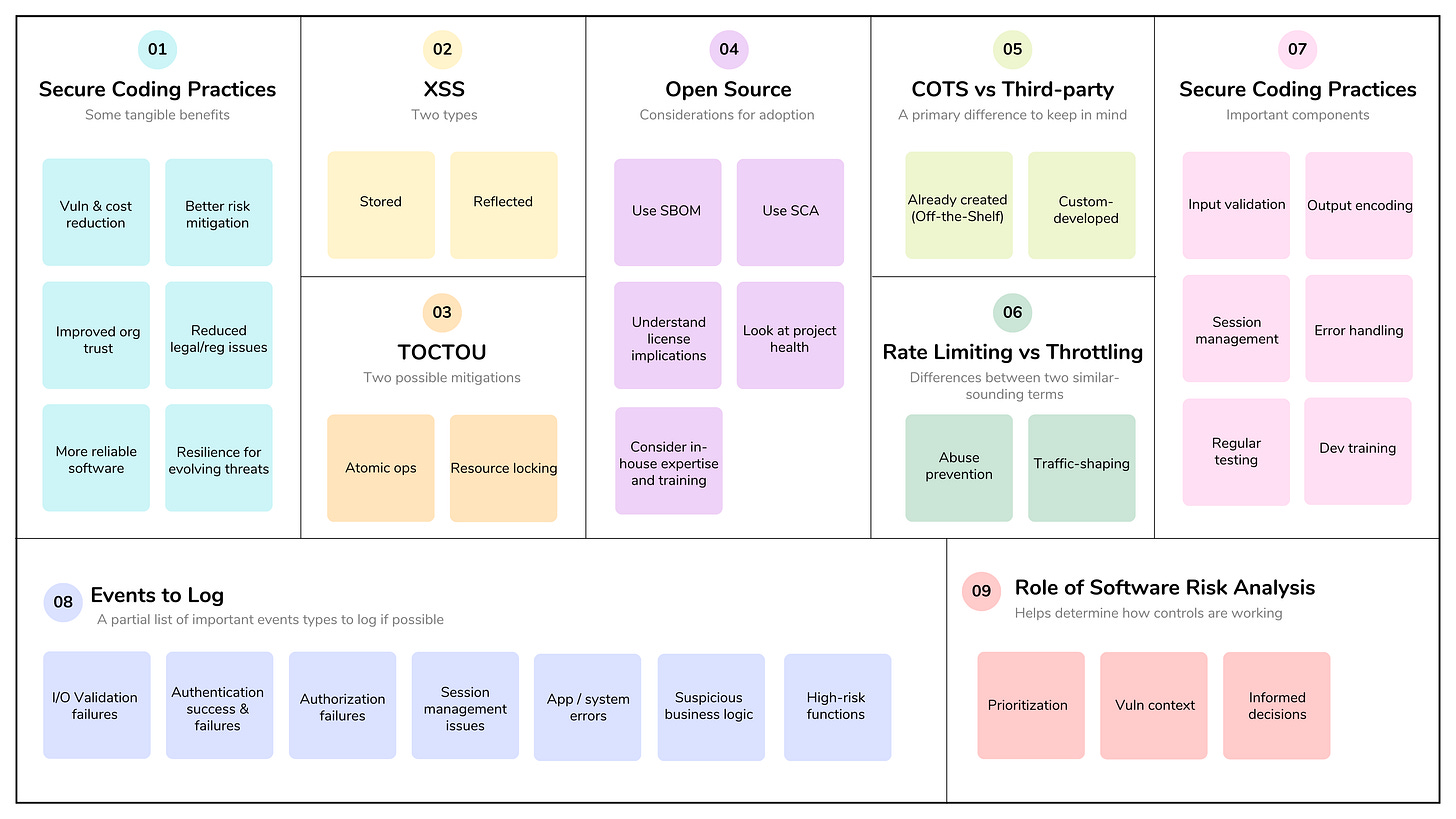
Assessing the effectiveness of software security relies on robust auditing and logging. Applications should be configured to log details of errors and other security events to a centralized log repository. Some security use cases include identifying security incidents, monitoring for policy violations, creating audit trails (e.g., data additions, modifications, deletions), compliance monitoring, risk analysis and mitigation, and attack detection.
Logs provide a definitive record of "who did what, when, and from where," preventing denial of actions after a security incident. In the wake of a breach, audit trails act as a primary source of truth, allowing teams to reconstruct timelines, identify initial entry points, and determine the full scope of compromised data. Real-time log monitoring can reveal suspicious patterns, such as access to sensitive files outside of normal business hours or a high volume of failed login attempts.
Key Considerations for Auditing Changes