Understanding CISSP Domain 1: Security and Risk Management
Security and Risk Management is the foundation of the CISSP — the domain upon which everything else is built. Representing 16% of the exam, it not only carries the heaviest weight but also shapes how you think like a security leader. By mastering its fundamentals — from governance to risk management — you establish the backbone of both your exam success and your ability to align security with business strategy.
Let’s dive into the domain and cover the material by following the ISC2 exam outline.
1.1 Understand, adhere to, and promote professional ethics
At the top of the list of important concepts is the idea that ethics matter, and organizations have laws and security policies that are crucial for maintaining the integrity of data and system security.
ISC2 Code of Professional Ethics
You need to understand the Preamble and the Code of Professional Ethics thoroughly in the context of corporate and industry applications. You should also memorize the Code of Ethics Canons in order:
Organizational code of ethics
You must also support ethics at your organization. This can involve backing and reinforcing ethics throughout the organization, providing documentation and training on ethics, or exploring ways to enhance existing organizational ethics.
1.2 Understand and apply security concepts
Confidentiality, integrity, and availability, authenticity, and nonrepudiation (5 Pillars of Information Security)
The CIA Triad (part of the Five Pillars) is the cornerstone of information security that supports the design, structure, and implementation of security. These three principles are the primary goals of secure systems and infrastructure.
Five Pillars of Information Security
The five (5) Pillars of Information Security are confidentiality, integrity, availability, authenticity, and nonrepudiation.
Here’s what those terms mean:
Confidentiality: the principle that objects should not be disclosed to unauthorized subjects, and includes the measures used to ensure the protection of the secrecy of data, objects, and resources.
Integrity: the idea of protecting the reliability and correctness of data, and guarding against unauthorized or improper modification or destruction. This includes preventing authorized subjects from making unauthorized modifications (including mistakes).
Availability: authorized subjects should be granted timely and uninterrupted access to objects.
Authenticity: ensuring a transmission, message, or sender is legitimate.
Nonrepudiation: the subject of an activity or who caused an event cannot deny that the event occurred. Nonrepudiation is made possible through the combination of identification, authentication, authorization, accountability, and auditing.
EXAM TIP: When you see “nonrepudiation”, think “proof of origin + accountability”. It’s not just about access, but also about ensuring that no one can deny their actions once they are completed.
You should also understand AAA Services.
AAA stands for Authentication, Authorization, and Accounting (or Accountability). In CISSP, it’s often extended to include Identification and Auditing. These services control who can access a system, what they can do, and how their actions are tracked.
AAA ensures secure access control and traceability in systems. It’s about users and their interactions with resources.
EXAM TIP: The key difference between AAA services and the Five Pillars:
AAA services are the mechanisms (how access control and accountability are enforced).
Five Pillars are the objectives (the ultimate security goals you’re trying to achieve).
1.3 Evaluate, apply, and sustain security governance principles
Alignment of the security function to business strategy, goals, mission, and objectives
Security governance flows directly from the organization’s mission, goals, and objectives.
Think about it like setting the rules and strategies that guide an organization’s security decisions. Security governance is used to make security decisions in an organization, support security efforts, and is aligned in every way with the business’s mission/vision, strategy, goals, and objectives. It’s not just about managing day-to-day security tasks - it’s about ensuring that security aligns with business goals, risks are effectively managed, and the company remains compliant with regulations.
Organizational processes (e.g., acquisitions, divestitures, governance committees)
Security governance should encompass every aspect of an organization, including its organizational processes related to acquisitions, divestitures, and governance. Understand that there are inherent risks in acquisitions, since the state of the target IT environment to be integrated is unknown. Due diligence is always key. Divestitures also carry risk and complexities as the organization contemplates how to split the IT infrastructure and determines what to do with important identities and credentials.
Organizational roles and responsibilities
For the exam, be familiar with these roles:
Senior Manager: the owner, accountable for security, policy authorization, associated resources, and exercising due diligence and due care.
Security Professional: the implementer, responsible for designing and implementing security solutions based on the security policy. The security professional has functional responsibility for security.
Asset Owner: the classifier, usually a high-level manager who is responsible for classifying information and determining appropriate asset protection. The asset owner often delegates data management tasks to a custodian.
Custodian: the doer, responsible for the task of implementing the protection defined by the security policy and senior management.
Auditor: the checker, responsible for reviewing and verifying that the security policy is properly implemented
User: anyone who has access to the secured system, responsible for following and upholding the organization’s security policy. User access should be limited to only what is strictly necessary to complete their job (principle of least privilege).
Security control frameworks (e.g., International Organization for Standardization (ISO), National Institute of Standards and Technology (NIST), Control Objectives for Information and Related Technology (COBIT), Sherwood Applied Business Security Architecture (SABSA), Payment Card Industry (PCI), Federal Risk and Authorization Management Program (FedRAMP))
International Organization for Standardization (ISO): a group of standards bodies from over 160 countries that bring global experts together to agree on best practices across a range of industries, including international standards, voluntary technical specifications, and guides. Some of the applicable standards include ISO 27001 (a global benchmark standard for creating an ISMS), and ISO 42001 (a framework for AI system management).
The National Institute of Standards and Technology (NIST) develops measurements, cybersecurity standards, guidelines, best practices, and other resources for federal agencies and the public. NIST produces 800-series special publications that provide technology-related standards and guidance, including the Cybersecurity Framework (CSF), and 800-53 (Security and Privacy controls).
COBIT (Control Objectives for Information and Related Technologies): a framework created by ISACA that focuses on enterprise IT, aligning IT and business strategies, and providing a comprehensive framework for managing risks.
Sherwood Applied Business Security Architecture (SABSA): a framework and methodology for developing business-driven, risk and opportunity-focused architectures for security and risk management.
Payment Card Industry Data Security Standard PCI DSS: a set of standards and requirements that endeavors to protect credit & debit card info.
Federal Risk and Authorization Management Program (FedRAMP): a government-wide program that standardizes the security assessment, authorization, and monitoring of cloud services and products. The program was established in 2011 to help the federal government use cloud technologies while protecting federal information.
Due care/due diligence
Due care and due diligence are essential concepts for thinking like a security manager or owner.
Due Diligence is about establishing a plan, policy, and processes to protect the organization’s interests. In other words, it’s knowing what should be done and planning for it. Examples of due diligence include
Doing discovery and risk assessments for an acquisition or merger.
Developing a formalized security structure that includes a security policy, standards, baselines, guidelines, and procedures.
Due Care is the practice of individual activities that maintain or carry out due diligence. Due care is about the legal responsibility within the law or within an organization’s policies to implement controls, follow security policies, and make reasonable choices.
Due care is the responsible protection of assets. Due diligence is the ability to prove due care.
1.4 Understand legal, regulatory, and compliance issues that pertain to information security in a holistic context
Cybercrimes and data breaches
You should understand the notification requirements placed on organizations that experience a data breach, and the following laws:
Computer Fraud and Abuse Act (CFAA): a US federal cybersecurity bill enacted in 1986, designed to protect computers used by the government or in interstate commerce from a variety of abuses.
National Information Infrastructure Protection Act: passed in 1996 as an additional set of CFAA amendments, including coverage of computer systems used in international commerce, protections for additional national infrastructure, and treating as a felony any act that causes damage to critical national infrastructure.
California’s SB 1386: which implemented the first statewide requirement to notify individuals of a breach of their personal information.
The HIPAA Breach Notification Rule: requires covered entities (like healthcare providers) and their business associates to notify affected individuals, the HHS Secretary, and sometimes the media about impermissible uses or disclosures of Protected Health Information (PHI) that compromise its security or privacy. Notifications must occur without unreasonable delay, but no later than 60 days after the discovery of the breach, and must include specific information about the breach and steps to take to protect oneself.
Council of Europe Convention on Cybercrime: a treaty signed by many countries that establishes standards for cybercrime policy.
Health Information Technology for Economic and Clinical Health (HITECH): an act that expanded HIPAA’s breach reporting.
Licensing and Intellectual Property requirements
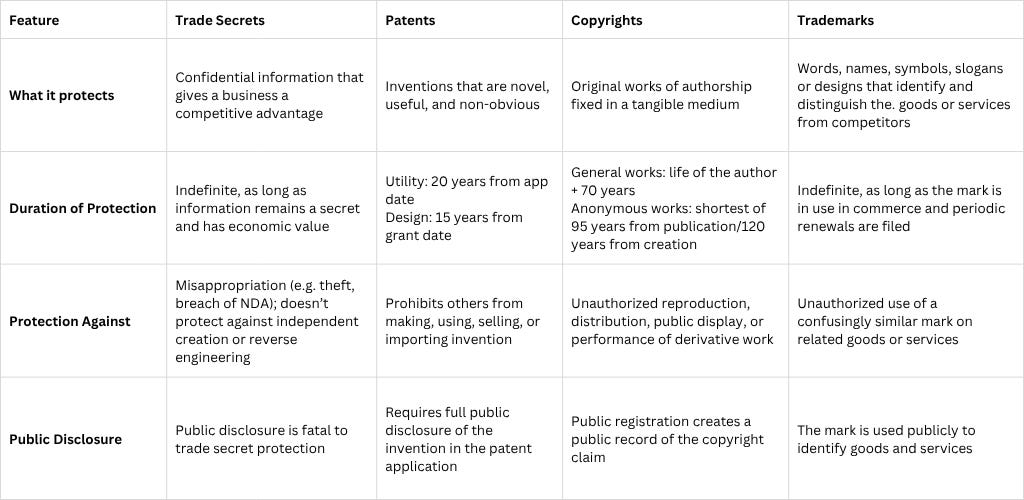
You should understand the differences between trade secrets, patents, copyrights, and trademarks.
Intellectual property: intangible assets (e.g., software, data, patents, etc.).
Trade Secret: confidential information that provides a competitive advantage because it is not generally known and has economic value. To be a trade secret, the owner must make reasonable efforts to keep the information secret, and the information must derive actual or potential value from its secrecy.
Patent: provides protection to the creators of new inventions, providing a temporary monopoly for producing a specific product or item, which must be novel and unique.
Copyright: the legal right granted to creators for their original works of authorship, giving them exclusive control over its reproduction, distribution, performance, display, and adaptation. This “bundle of rights” protects artistic, literary, musical, dramatic, and certain intellectual works, but not the underlying ideas themselves.
Trademark: words, slogans, and logos used to identify a company and its products or services.
Import/export controls
Every country has laws around the import and export of technology, products, and information. You should be familiar with ITAR, the Wassenaar Arrangement, and EAR.
International Traffic in Arms Regulations (ITAR): a US regulation controlling the manufacture, export, and import of military or defense items.
Wassenaar Arrangement: a multinational agreement and voluntary export control, the purpose of the Wassenaar Arrangement is to promote transparency and responsibility in the global trade of conventional arms and dual-use goods and technologies. It provides a forum for participating states to exchange information and coordinate national export controls to prevent destabilizing accumulations of arms and the proliferation of weapons of mass destruction.
The Export Administration Regulations (EAR): a U.S. Department of Commerce regulation enforced by the Bureau of Industry and Security (BIS) to control the export, reexport, and in-country transfer of commercial items and some military items that have both commercial and military uses.
Transborder data flow
Primarily related to personal data, transboundary data flow laws restrict the movement of data across country borders. When sharing data across borders, applicable laws should be considered.
Companies should adhere to origin country-specific laws and regulations, regardless of where data resides, and be aware of applicable laws where data is stored and systems are used.
Issues related to privacy (e.g., General Data Protection Regulation (GDPR), California Consumer Privacy Act, Personal Information Protection Law, Protection of Personal Information Act)
The purpose of the General Data Protection Regulation (GDPR), is to provide a single, harmonized law that covers data throughout the EU.
These principles form the foundation of GDPR compliance:
Lawfulness, Fairness, and Transparency: Processing must have a legal basis, be fair to individuals, and be transparent about how data is collected and used.
Purpose Limitation: Data should be collected for specific, explicit, and legitimate purposes.
Data Minimisation: Personal data should only be collected and processed for the minimum amount necessary for the purpose.
Accuracy: Personal data must be accurate, kept up-to-date, and corrected or deleted when necessary.
Storage Limitation: Data should only be stored for as long as it’s needed for its original purpose.
Integrity and Confidentiality: Organizations must protect personal data from unauthorized access, loss, or destruction using appropriate security measures.
Accountability: Organizations must be able to demonstrate compliance with all the GDPR principles and have measures in place to ensure adherence.
The GDPR’s privacy rules apply to any organization, regardless of its location, that stores or processes the personal data of EU residents.
The key aspects of the California Consumer Privacy Act (CCPA) grant California residents rights over their personal data, including the right to know what information is collected, the right to delete their data, the right to correct it, and the right to opt out of the sale or sharing of their data. The CCPA also includes a right to limit the use of sensitive personal information and prohibits businesses from discriminating against consumers who exercise their rights.
The Personal Information Protection Law (PIPL) is a comprehensive Chinese data privacy law with similarities to GDPR.
The Protection of Personal Information Act (POPIA) is South Africa’s comprehensive data protection law designed to protect personal information processed by public and private entities, and promote the right to privacy.
Contractual, legal, industry standards, and regulatory requirements
You should understand the difference between criminal, civil, and administrative law
Criminal law: protects society against acts that violate the basic principles we believe in, and violations of criminal law are prosecuted by federal and state governments.
Civil law: provides the framework for the transaction of business between people and organizations. Violations of civil law are brought before the court and argued by the two parties affected.
Administrative law: used by government agencies to effectively carry out their day-to-day business.
Organizations may be subject to a wide range of contractual obligations, laws, and regulations imposed by regulatory agencies.
In the US, regulatory requirements play a significant role in shaping security governance. Non-compliance can result in substantial fines and damage to an organization’s reputation.
HIPAA (Health Insurance Portability and Accountability Act): This law governs healthcare organizations and their business associates, requiring safeguards for electronic protected health information (ePHI). Organizations must conduct risk assessments, implement access controls, and maintain audit logs. Fines for violations can be high.
SOX (Sarbanes-Oxley Act): Applicable to publicly traded companies, SOX focuses on financial reporting and internal controls. Section 404 requires management to assess and report on the effectiveness of internal controls over financial reporting (ICFR), which includes IT controls like change management and access controls, as these are critical for preventing errors or fraud in financial reporting.
GLBA (Gramm-Leach-Bliley Act): This law requires financial institutions to protect customer information. The GLBA Safeguards Rule requires financial institutions to implement a comprehensive, written information security program to protect the confidentiality, integrity, and security of their customers’ nonpublic personal information (NPI).
PCI DSS (Payment Card Industry Data Security Standard): Though not a federal regulation, this industry standard applies to organizations handling credit card data. Compliance is contractually required by card brands and encompasses 12 key requirements that cover areas such as network security, data protection, and access controls.
1.5 Understand requirements for investigation types (i.e., administrative, criminal, civil, regulatory, industry standards)
Investigation details will vary based on incident type; however, they usually share common goals such as gathering evidence, identifying involved parties, and recommending actions.
Investigation types include:
Administrative: internal investigations usually review operational issues or violations of an organization’s policies and, compared to other types, have the lowest formality for documentation and procedures.
Criminal: requires adherence to strict procedures to ensure court admissibility and is conducted by law enforcement; a suspect must be proven guilty beyond a reasonable doubt.
Civil: conducted by lawyers or private investigators to gather evidence, establish liability, and determine damage or liability amounts. In a civil case, a preponderance of evidence is required to secure a victory.
Regulatory: an investigation that is conducted by a regulatory body, such as the Securities and Exchange Commission (SEC) or Financial Industry Regulatory Authority (FINRA), against an organization suspected of an infraction.
Industry Standards: an investigation intended to determine whether an organization is adhering to a specific industry standard or set of standards, such as those associated with PCI DSS. Because standards are not laws, these investigations can be related to contractual compliance, and a business may be required to participate in audits or assessments to ensure compliance.
1.6 Develop, document, and implement security policy, standards, procedures and guidelines
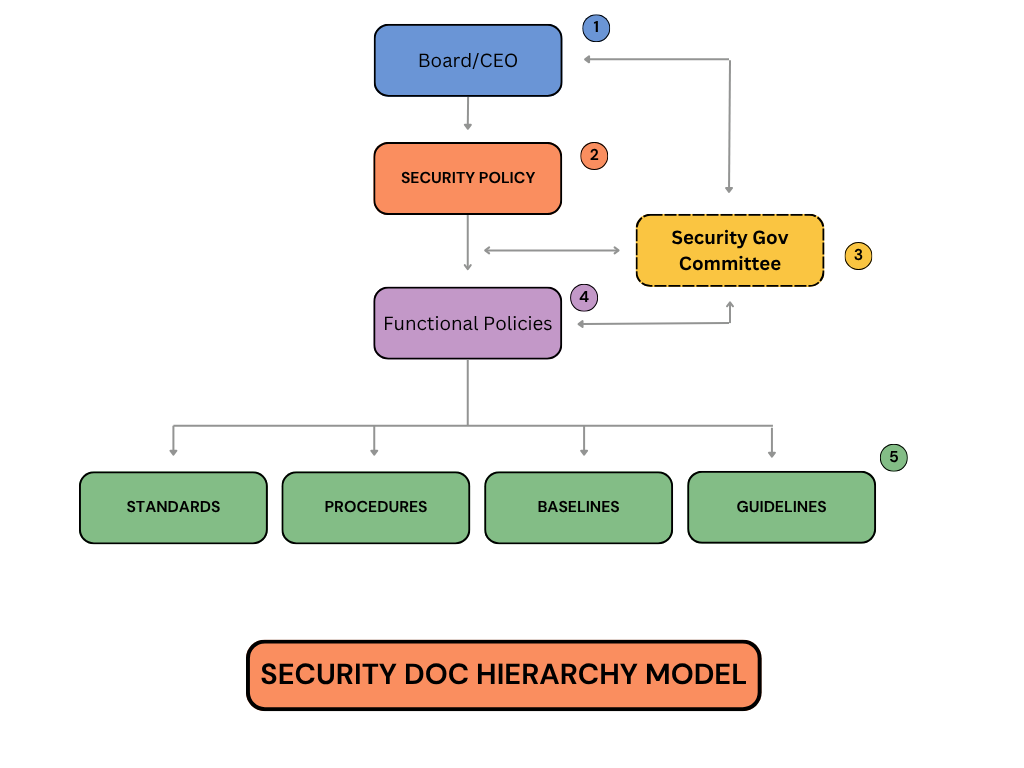
Policies, standards, procedures, baselines, and guidelines are important parts of a comprehensive security plan. The top tier of a formalized security documentation hierarchy is the security policy.
A security governance document hierarchy is a structure in which policies cascade from senior management to actionable controls, providing a clear framework for implementing and enforcing security measures.
Board & CEO (define business risk appetite): the board and CEO provide the overall strategic direction for the business and define its risk tolerance.
CISO + Senior Management (draft & approve enterprise security policy): with executive oversight, the security policy is created, ensuring that it is aligned with and supports the company’s strategic goals and regulatory obligations.
Corporate Security Governance Committee (develop functional security policies): after the overarching security policy is established by top leadership, a security governance committee—often composed of the CISO and other cross-functional executives—takes the lead on functional policy creation and implementation.
Functional Policies (access control, data classification, incident response, etc.): the security governance committee uses the overarching policy to create more specific policies for functional areas, such as access control, incident response, or data protection.
Standards → Procedures → Baselines → Guidelines (detailed implementation controls): supporting documents are derived from policies.
Here is a further breakdown of each:
Policy: A security policy is a document that defines the scope of security needed by the organization, discussing assets that require protection and the extent to which security solutions should go to provide the necessary protection.
Standard: More descriptive than a policy, a standard is a specific mandate explicitly stating expectations of performance in the organization. A standard defines the compulsory requirements for the use of technology and systems, as well as the security controls used throughout the organization.
Baseline: A baseline defines a minimum level of security that every system throughout the organization must meet.
Guideline: A guideline is a recommendation on how standards and baselines should be implemented, and serves as an operational guide for security professionals and users.
Procedure: A procedure is a detailed, step-by-step description of the exact actions necessary to implement a specific security mechanism, control, or solution.
1.7 Identify, analyze, assess, prioritize, and implement Business Continuity (BC) requirements
Business Continuity Planning (BCP) involves assessing the risk to organizational processes and creating policies, plans, and procedures to minimize the impact of those risks. The four major steps of BCP are:
1) Project scope and planning
2) Business impact analysis (BIA)
3) Continuity planning
4) Approval and implementation
Business impact analysis (BIA)
The BIA is used to identify critical business functions and processes, determine dependencies between them, assess potential impacts on the disruption of those functions and processes, identify maximum tolerable downtime for each, and prioritize business recovery based on function criticality.
External dependencies
Understanding the roles and responsibilities of third parties is an essential part of the BCP process, as it enables you to plan for how these organizations and their associated services will impact your contingency plans. It’s essential to evaluate external parties and vendors, assess their criticality to the business, and prioritize those that could have a significant impact if their services were disrupted. This should include vendors of critical hardware and software, cloud providers, transportation and logistics providers, utilities, and financial-related providers.
1.8 Contribute to and enforce personnel security policies and procedures
Candidate screening and hiring
People are often considered the weakest element in any security solution, and new personnel represent a greater risk to security. People can also become a key security asset when they are properly trained and motivated to protect not only themselves but also the organization's security.
Thoroughly screening employment candidates is a crucial part of the hiring process, which should include background checks, job history verification, education verification, and reference checks.
Part of planning for security includes having standardized job descriptions, job classifications, and procedures such as candidate screening, background checks, security clearances, and employment agreements.
Employment agreements and policy-driven requirements
Agreements and policies provide expectations for employees and protect an organization’s interests. Employment agreements outline job duties, expectations, compensation, benefits, and details regarding termination. Sometimes, such agreements are for a set period (for example, in a contract or short-term job). Non-disclosure agreements (NDAs) are used to protect confidential information, and acceptable-use policies (AUPs) define a level of acceptable performance and expectation of behavior and activity.
Mandatory vacations are often included in employment policies to help detect fraud and audit an employee’s work.
Onboarding, transfers, and termination processes
Onboarding is the process of bringing a new employee into the business.
An employee transfer refers to the process of moving from one job to another. A transferring employee will likely require adjusted account access to maintain appropriate least privilege.
Termination or offboarding refers to the removal of an employee’s identity from an IAM system after they have left the organization. It can also be an element used when an employee transfers into a new role.
Vendor, consultant, and contractor agreements and controls
Information security policies and procedures should address outsourcing security and the use of service providers, vendors, and consultants. Examples include access control, document exchange and review, maintenance, on-site assessment, process and policy review, and Service Level Agreement (SLA) reviews, all of which are examples of outsourcing security considerations.
1.9 Understand and apply risk management concepts
Threat and vulnerability identification
An asset is anything of value. The monetary valuation of an asset for calculation purposes is referred to as asset value (AV).
The attack surface is the totality of entry points an attacker can exploit to get access to a system. The potential consequences of a successful attack, such as financial loss and reputational harm, are collectively referred to as its impact.
Risk Management is the process of identifying factors that could damage assets or disclose information. Risk is the possibility that a threat will exploit a vulnerability to cause harm to an asset.
A threat is any potential occurrence that may cause an undesirable or unwanted outcome for a specific asset.
A vulnerability is a weakness in an asset, or the absence of a safeguard or countermeasure that could be exploited.
Exposure refers to the degree to which an asset is accessible or vulnerable to a threat.
Threats and vulnerabilities are related: a threat is possible when a vulnerability is present. Threats exploit vulnerabilities, which results in exposure. Exposure is risk, and risk is mitigated by safeguards.
The Exposure Factor (EF) represents the percentage loss an organization would experience if a specific asset were violated by a realized risk.
Single Loss Expectancy (SLE) is equal to Asset Value (AV) multiplied by the Exposure Factor (EF).
The Annualized Rate of Occurrence (ARO) represents the expected frequency with which a specific threat or risk is anticipated to occur in a single year.
The Annualized Loss Expectancy (ALE) represents the potential yearly costs of all instances of a specific realized threat against a particular asset and is calculated as follows: ALE = SLE × ARO.
Risk analysis, assessment, and scope
A Risk Assessment is used to identify risks and set criticality priorities. Risk Analysis is the examination of factors such as the likelihood and impact of identified risks.
Risk is a threat multiplied by a vulnerability (or probability of harm multiplied by severity of harm). There are two primary risk-analysis methodologies:
Quantitative Risk Analysis assigns real monetary figures to the loss of an asset and is based on mathematical calculations.
Qualitative Risk Analysis assigns subjective and intangible values to the loss of an asset, usually based more on scenarios than calculations, and threats are ranked to evaluate risks, costs, and effects.
Risk response and treatment (e.g., cybersecurity insurance)
A Risk Response is used to determine the best defense for each identified risk. The primary risk response and treatment strategies are:
Avoidance: determining that the impact or likelihood of a specific risk is too great to be offset by potential benefits, and not performing a particular business function due to that determination.
Risk Exploitation: taking on a risk and assuming a positive outcome or return.
Risk Mitigation: the implementation of safeguards, security controls, and countermeasures to reduce and/or eliminate vulnerabilities or block threats.
Risk Transference: paying an external party (i.e., an insurance company) to accept the financial impact of a given risk.
Risk Acceptance: deciding not to take action to mitigate a risk.
Risk Rejection: an unacceptable possible response is to reject risk or ignore risk; denying that risk exists and hoping that it will never be realized are not valid prudent due care/due diligence responses to risk.
Applicable types of controls (e.g., preventive, detection, corrective)
Preventive: deployed to thwart or stop unwanted or unauthorized activity from occurring.
Deterrent: control that is deployed to discourage security policy violations; deterrent and preventative controls are similar, but deterrent controls often depend on individuals being convinced not to take an unwanted action.
Directive: control that is deployed to direct, confine, or control someone’s actions to force or encourage compliance with security policies.
Detective: a control that is deployed to discover or detect unwanted or unauthorized activity; detective controls operate after the fact.
Corrective: a corrective control modifies the environment to return systems to normal after an unwanted or unauthorized activity has occurred.
Recovery: an extension of corrective controls that attempts to repair or restore resources, functions, and capabilities after a security policy violation.
Compensating: an alternative security measure implemented when a primary or standard security control can’t be fully implemented or is impractical to deploy.
Control assessments (e.g., security and privacy)
A Security Control Assessment (SCA) is a formal evaluation and review of individual controls against a baseline to ensure the effectiveness of security mechanisms, assess the quality of the risk management process, and generate a findings report.
Continuous monitoring and measurement
Monitoring and measurement are closely aligned with identifying risks. While monitoring is used for more than security purposes, monitoring should be tuned to ensure the organization is notified about potential security incidents as soon as possible. Monitored systems and data become valuable from a forensic perspective in the event of a security breach.
Reporting (e.g., internal, external)
Risk Reporting (creation and presentation of a summarizing report) is a key task to perform at the conclusion of risk analysis. Note that risk reports for internal audiences can contain sensitive information, and distribution should be controlled for only those who need to know.
Continuous improvement (e.g., risk maturity modeling)
Risk analysis is performed to provide management with the details necessary to decide how to address risks and which require specific treatment. A Risk Maturity Model (RMM) is used to assess the key indicators and activities of a mature, sustainable, and repeatable risk management process.
Risk frameworks (e.g., International Organization for Standardization (ISO), National Institute of Standards and Technology (NIST), Control Objectives for Information and Related Technology (COBIT), Sherwood Applied Business Security Architecture (SABSA), Payment Card Industry (PCI))
A risk framework serves as a guide or set of best practices for assessing, measuring, and monitoring risk. While the frameworks are defined above, here are some key details on each:
The International Organization for Standardization (ISO) develops and publishes several important security standards, such as 27001, 27002. ISO 31000 specifically provides principles and guidelines for an enterprise risk management framework and associated processes.
NIST SP 800-37 provides the overarching Risk Management Framework (RMF), outlining the process for assessing and managing information system risks, while NIST SP 800-53 provides the detailed catalog of security and privacy controls to be selected and implemented as part of that framework. The RMF has 7 steps:
Prepare
Categorize
Select
Implement
Assess
Authorize
Monitor
Control Objectives for Information and Related Technology (COBIT) is a comprehensive set of guidelines for IT Governance and management with five domains:
Evaluate, Direct, and Monitor
Align, Plan, and Organize
Build, Acquire, and Implement
Deliver, Service, and Support
Monitor, Evaluate, and Assess
Sherwood Applied Business Security Architecture (SABSA) is an open enterprise security architecture methodology with five security architecture phases:
Contextual
Conceptual
Logical
Physical
Component
The Payment Card Industry (PCI) issues the standard, which is applicable to any organization that processes, transmits, or stores cardholder data.
1.10 Understand and apply threat modeling concepts and methodologies
Threat Modeling is a structured approach to identifying potential system or software security threats. An organization’s security posture can be improved by proactively analyzing and categorizing these threats. Threat modeling can be performed as a proactive measure during design and development, and as a reactive measure once a product has been deployed.
Some common threat modeling methodologies include:
DREAD (Damage potential, Reproducibility, Exploitability, Affected users, and Discoverability): a Microsoft- developed threat modeling approach to detect and prioritize threats so that serious threats can be mitigated first.
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): a risk-based framework for identifying, analyzing, and mitigating cybersecurity risks, developed by Carnegie Mellon University. It’s three phases:
Build Asset-Based Threat Profile
Identify Infrastructure Vulnerabilities
Determine Security Risk Management Strategy
PASTA (Process for Attack Simulation and Threat Analysis): a seven-stage threat modeling methodology:
Define business objectives
Define technical scope
Decompose application
Analyze threats
Identify vulnerabilities
Enumerate attacks
Perform impact analysis
STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Elevation of privilege) is a framework for identifying and categorizing security threats based on their nature and potential impact.
Trike: an open source risk-based threat modeling methodology. Trike provides a method for performing a reliable and repeatable security audit, as well as a framework for collaboration and communication.
VAST (Visual, Agile, and Simple Threat): a threat modeling concept that integrates threat and risk management into an Agile programming environment on a scalable basis.
Part of the job of the security team is to identify threats, using different methods:
Focus on attackers: this is a useful method in specific situations, such as trying to understand a particular attacker or threat.
Focus on assets: an organization’s most valuable assets are likely to be targeted by attackers.
Focus on software: the goal isn’t to identify every possible attack, but to focus on the big picture, identifying application risks and attack vectors.
1.11 Apply Supply Chain Risk Management (SCRM) concepts
Supply Chain Risk Management (SCRM) is the process of identifying, assessing, and mitigating risks associated with an organization’s supply chain — including third-party vendors, service providers, manufacturers, and partners — to ensure the confidentiality, integrity, and availability (CIA) of systems, data, and services.
SCRM involves implementing policies, controls, and monitoring mechanisms to reduce the risk introduced by external dependencies, such as:
Hardware and software components
Cloud and managed service providers
Logistics and distribution partners
Outsourcing and subcontracting arrangements
Risks associated with the acquisition of products and services from suppliers and providers (e.g., product tampering, counterfeits, implants)
The supply chain can be a threat vector, where materials, software, hardware, or data are obtained from a supposedly trusted source, but the supply chain behind the source could have been compromised, allowing the asset to be poisoned or modified.
Supply chain attacks encompass various forms, including:
Product tampering: the intentional modification, alteration, or manipulation of a legitimate product (hardware, software, or service) after it has been manufactured or during distribution, with the goal of introducing malicious functionality, defects, or vulnerabilities.
Counterfeits: unauthorized copies or imitations of genuine products that are designed to look legitimate but are manufactured without proper quality assurance, certification, or authorization. These may introduce security vulnerabilities or fail under critical conditions.
Implants: malicious hardware or software components deliberately inserted into a product (at design, manufacturing, or distribution stages) to provide unauthorized access, data exfiltration, surveillance, or control.
These attacks can be difficult to detect, and changes or manipulations can be made via hardware (even miniaturized chips) or via software.
Risk mitigations (e.g., third-party assessment and monitoring, minimum security requirements, service level requirements, silicon root of trust, physically unclonable function, software bill of materials)
Third-Party Assessment and Monitoring: independent reviews (audits, compliance assessments) and continuous oversight of suppliers and service providers to ensure they meet security, legal, and contractual obligations.
Minimum Security Requirements: baseline security controls and practices that suppliers must implement before doing business with the organization.
Service Level Requirements (SLRs): detailed, measurable security and performance obligations defined in a contract (often part of a Service Level Agreement, SLA). An SLR should include capabilities and performance metrics for areas such as disaster recovery and incident response.
Silicon Root of Trust (SRoT): a hardware-based security mechanism (part of trusted platform modules (TPMs), or hardware security modules (HSMs)) embedded into processors or chips during manufacturing, and used to establish a trusted baseline for booting systems.
Physically Uncloneable Function (PUF): A unique hardware identifier derived from random variations in semiconductor manufacturing, which cannot be duplicated (even by the manufacturer). A PUF can serve as a unique authentication identifier for an SRoT.
Software Bill of Materials (SBOM): A formal, structured list of all components, libraries, dependencies, and modules that make up a software product.
For the exam: Remember that management (the organization) is always ultimately responsible for managing supply chain risks, even if vendors or third parties cause the issue.
1.12 Establish and maintain a security awareness, education, and training program
Methods and techniques to increase awareness and training (e.g., social engineering, phishing, security champions, gamification)
Users should receive training during onboarding, as well as periodic refresher training, even if it’s just an email reminding them of the threats.
There are several proven techniques to improve user awareness and training:
Security Awareness Training: security knowledge for employees that can take the form of short, role-specific training, or on-demand training videos and courses covering things like phishing, social engineering, and how to stay safe.
Targeted Awareness Campaigns: can include phishing and social engineering simulations, posters, newsletters, and messages that reinforce key security practices visually and regularly.
Role-Specific Training: providing targeted training by role, including password hygiene, phishing recognition, reporting suspicious behavior for general employees; risk management, legal/regulatory responsibilities, reputational impacts for leadership; secure coding practices, OWASP Top 10, SBOM awareness for developers; and incident response, system hardening, and access management for IT ops.
Gamification: using points, leaderboards, badges, or competitions for completing training as a method of increasing engagement.
Security Champions Program: embedding trained advocates within business units who promote good practices.
Periodic content reviews to include emerging technologies and trends (e.g., cryptocurrency, artificial intelligence (AI), blockchain)
It’s essential to provide ongoing education to staff about emerging technologies and trends to stay ahead of evolving threats and best practices for effective cybersecurity hygiene.
Program effectiveness evaluation
Best practices for evaluating the effectiveness of your security awareness, education, and training program include:
Define clear objectives and metrics: Set measurable goals before launching the program (e.g., reduce phishing click rates, increase reporting of suspicious activity), and use specific, measurable, achievable, relevant, time-bound metrics.
Track completion rates and assessment testing: measure completion of e-learning modules, acknowledgment of policy reviews, and quizzes to assess employee understanding and retention.
Request qualitative feedback: collect feedback via surveys, focus groups, or informal discussions.
For the exam, if a question asks about improving awareness/training, the best answers will usually emphasize ongoing, role-based, engaging, and measurable programs (as opposed to one-time events).
If you’re on your CISSP journey, keep studying, keep connecting the dots, and take a look at my Guide to Security Governance — a core component of Domain 1.