Encryptionville
Encryptionville
Let’s stroll together through the sun-baked streets of a beautiful community with amazingly cool technology that shines under a sparkling blue sky. It’s a place called Encryptionville, where all the encryption is strong, all the code is good-looking, and all the bits are above average.
Here’s The Thing
Encryption is the process of scrambling a message so that only certain people can understand it. We use encryption to keep data secure when we shop or bank online, ensuring hackers can't misuse our information.
Why Encryption?
Encryption is used to protect data or safeguard confidential information from unauthorized access. Whether data is stored on devices (known as data at rest) or transmitted over networks (known as data in transit), we use encryption to ensure that if data is intercepted, it remains unreadable without the appropriate key. This protects personally identifiable information (PII), financial records, and sensitive corporate data.
Encryption can also lower the risk of a data breach by making the stolen data worth less to attackers. If hackers encounter encrypted data at rest, it’s harder to leverage in a ransomware event.
Encryption is vital to industries subject to regulations such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR). These regulations require the protection of sensitive data through encryption, and compliance helps protect consumers and organizations avoid legal penalties.
When implemented and used correctly, encryption can improve customer loyalty. In a world of constant breach notifications, we all want companies to prioritize data security, and businesses that do so make it easier to attract customers and build market share.
The inhabitants of Encryptionville understand that while encryption is an essential tool, it isn’t the universal solution to all information security issues. When you log into your bank by confirming that you have the correct account credentials, your information is presented in a readable format. So, even though your bank may store and transmit your information securely using the most advanced encryption, the fact that you’ve authenticated to your account gives you unencrypted access.
In other words, encryption is irrelevant to safeguarding your data if someone has full access to your account. If a hacker can convince the bank that they are you, that is a much easier way to get access to your bank account than breaking industry-standard encryption.
A Short History of Encryption
The word encryption comes from the Greek kryptós, which means “hidden” or “secret.” It’s been used in various forms for a very long time. For example, Julius Caesar invented a famous cipher (a cipher is a disguised way of writing) that shifts characters by a specific number of places in the alphabet: for instance, A becomes D, B becomes E, etc.
Surprisingly, in the early 2000s, a Sicilian Mafia boss named Bernardo Provenzano used a variant of Mr. Caesar’s cipher to communicate coded messages. Now, using a cipher may have been effective back in 44 B.C. But it’s nothing like modern-day encryption; you won’t find anyone in Encryptionville using it. Unfortunately for Provenzano, his “pizzini code” only obfuscated his messages. We say that security through obscurity isn’t real security, and Bernardo found that out the hard way.
In the last 25 years, encryption, or rather cryptography, which is the science of concealing messages, has come a long way. Some excellent algorithms were invented, many of which you likely use daily. Let’s tiptoe a bit deeper into the cryptography weeds.
Types of encryption
Modern encryption works to secure communications (and to do other cool things — more on this later) because it uses hard-to-solve math problems. These problems are sort of like those that you encountered in high school algebra, but, well, harder.
At their essence, hard math enforces policies on information. They are so intractably complex that you can't make sense of the encrypted data unless you have a secret piece of information called a key.
There are two basic types of encryption: symmetric and asymmetric. The difference between the two simply relates to the number of keys used. Symmetric encryption keeps information private by using a shared secret: a single key for the encryption and decryption of a message. It is fast and efficient, but the key must be delivered and stored securely between parties. Asymmetric encryption, also called public key encryption, uses two separate keys, one public and one private.
Symmetric Encryption
Let’s talk through a simple example of using symmetric encryption. Let me introduce you to Betty and Bob.
Betty and Bob live in different but equally serene and leafy streets in Encryptionville. Let’s say that Betty wants to send a sensitive message to Bob, and she uses an encryption program to protect the message with a passphrase. She sends the encrypted message to Bob, but unfortunately, Bob can’t read it because he doesn’t know the passphrase or key Betty uses.
How can Betty securely share the key with Bob? She can’t email it because a third party could intercept and read messages sent between them. This is where asymmetric encryption solves the problem of key exchange.
Asymmetric Encryption
Here’s how it works: imagine houses on the streets of Encryptionville each have a mailbox. The mailbox’s location is public, and anyone who knows the address can go to it and drop off a message. However, only the mailbox owner has the key to open and read the messages.
Betty and Bob can generate a key pair on their computers using the RSA algorithm. RSA is a well-known public-key asymmetric cryptosystem used for secure data transmissions. The initials "RSA" come from the surnames of Ron Rivest, Adi Shamir, and Leonard Adleman, who publicly described the algorithm in 1977.
The RSA algorithm will generate a public and private key pair that is mathematically linked. Both Betty and Bob now each have a public and private key set. And even though each key pair is linked, one cannot be derived from the other. In other words, if someone knows Betty’s public key, they can’t figure out or derive her private key. The public key can encrypt data, and only the matching private key can decrypt it.
In Encryptionville, each mailbox’s address would be the public key, which everyone can find. The mailbox owner is the only one who has the private key, which is used to open that mailbox.

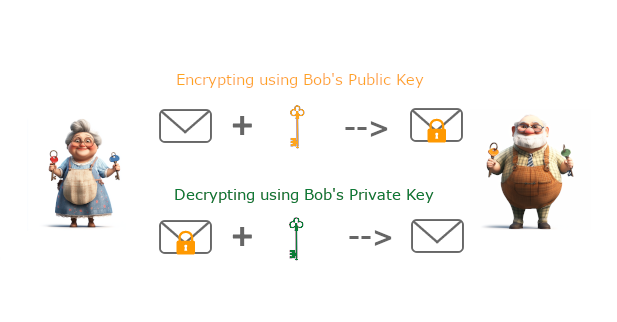
Using RSA, Betty and Bob can send encrypted messages as follows. They start by exchanging their public keys: Betty gives her public key to Bob, and Bob provides his public key to Betty.
Now, Betty can encrypt her message with Bob’s public key. She sends the message to Bob, who decrypts it with his private key, allowing him to unlock and read it. Only Bob can decrypt the message. Not even Betty can decrypt the message once it’s encrypted with Bob’s public key because she doesn’t have Bob’s private key.
The strength of asymmetric encryption depends on Bob and Betty keeping their private keys protected. If someone steals Bob’s private key, they could read anything intended for him that was encrypted using his public key.
Asymmetric encryption is used in many things you likely encounter daily, such as making purchases on the web or securely communicating with your bank. For instance, every time you visit a secure website using HTTPS, you are actually using asymmetric encryption. Asymmetric encryption is also an essential factor in sending and receiving Bitcoin and other cryptocurrency transactions.
Digital Signatures
We’ve talked about using encryption to keep messages private. Digital signatures are another encryption-related tool that allows us to confirm the identity of the message sender (known as authenticity), ensure that the message hasn’t been altered in transit (known as integrity), and prove that a signature was, in fact, generated by the claimed signatory. This is known as “non-repudiation” since the person who signed can’t easily deny the signature at a later time.
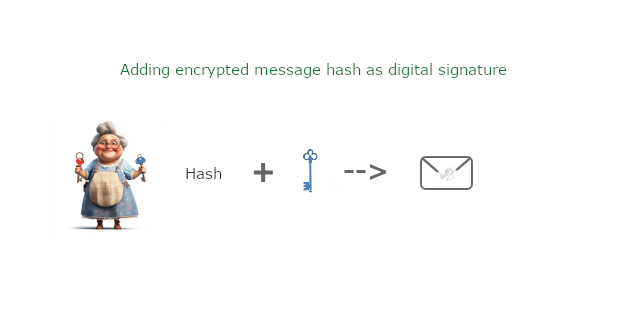
We can use a hash function to facilitate creating a digital signature. A hash is a fixed-length string generated from the original message. The hash is unique to the message; computing the hash of a message will return the same exact string, no matter how many times you do it. But even a tiny change in the message will produce a different hash.
We use asymmetric encryption to sign documents. Betty starts by creating a hash of her message. She then encrypts the hash using her private key to create a digital signature for her message. Her public key can be used to verify that the message was authored and signed by her.
TL;DR
We use encryption daily to keep data secure. Keeping secrets has been a human endeavor for thousands of years, and our ability to provide better methods of concealing information has taken significant strides in the last few years.
Modern encryption is based on difficult-to-solve math problems. It underlies much of what we do online, including sending secure messages, encrypting data when not in use, and acting as a digital signature.
Despite its many uses and benefits, encryption is not a fail-safe against all forms of attack. If an attacker can find, guess, or get you to provide the credentials to your account, that is likely a much easier way of accessing your data. So while the inhabitants of Encryptionville love their maths, they must also keep their account information private.
If you’re ever in Encryptionville, please give Betty and Bob our best. Compute safely, my friends!
I’m an IT and information security leader with over two decades of IT executive leadership and cybersecurity experience in multiple industries. If you enjoyed this article, consider subscribing to my blog, where I write about cybersecurity, and connect with me on LinkedIn. If you’re studying for the CISSP exam, look at my study resources on Git Hub, and reach out if you have questions. We can learn together! Thank you for reading.