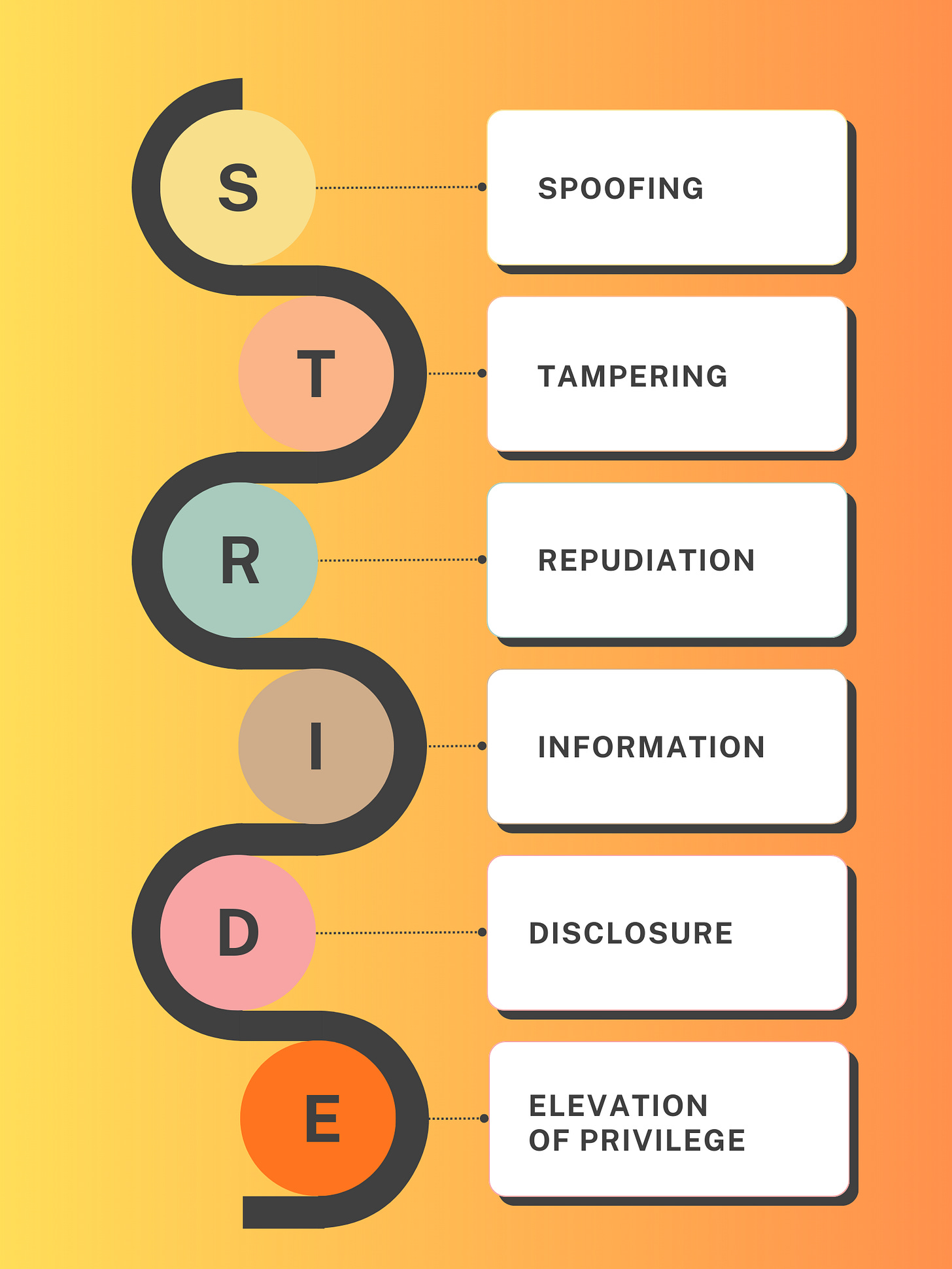
A CISSP Threat Modeling Primer
You Already Threat Model. You Just Don’t Call It That.
You own a retail store. Before opening day, you think about potential merchandise loss from shoplifting. You think about which products are expensive enough to warrant security tags. You think about whether the cheap lock on the back door is good enough, or whether something heavier is warranted. You don’t have a spreadsheet. But you’re doing something real: systematically thinking about what can go wrong, how badly, and what it’s worth spending to prevent it.
That’s threat modeling. Every formal framework we’re about to cover does this same thinking with more structure, more rigor, and a shared vocabulary. A vocabulary that lets teams see the same problems the same way.
As a CISSP exam candidate, you should be familiar with these threat models. And while you don’t need to be an expert in each, it helps to understand when they’re used and why.
Remember that the goal of threat modeling is simple: to reduce or eliminate threats.